What’s that about ? #
The THCon (Toulouse Hacking convention), is a French cybersecurity conference that brings together hobbyists, professionals and researchers every year at Toulouse in April.
This edition (2024), I was one of the challenge creators and (co-)created an OSINT challenge, a few steganography challenges, and a 4-step network challenge, which I’ll detail in the following blog post.
Note : the CTFd is not up anymore so if you did not participate, or you don’t remember the challenges you can take a look at https://ctftime.org/event/2269/tasks/ although not all of them are listed sadly :/
Step by step write-up #
Find me if you can #
For this step, all you had to do was open the file with wireshark, and you’d find the flag in clear text, along with the port to connect to for the next step.
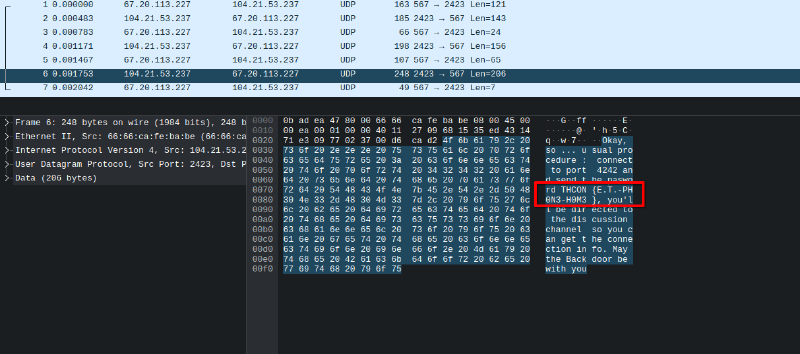
Let us Phone Home #
We connect to port 4242 and send the flag to connect, after which we retrieve the second flag. (This can also be done with netcat).
import socket
adresseIP = "20.19.38.158"
port = 4242
client = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
client.connect((adresseIP, port))
print("Connected to the server")
message = "THCON{E.T.-PH0N3-H0M3}"
client.send(message.encode("utf-8"))
received = client.recv(1024).decode()
print(received)When connecting you’d be greeted with the flag and also a message telling you that you can connect to the port 2647 using the new flag as a password to get the discussions of the villain’s team (yes, apparently they’re using the hacked satellites as a -way less secure- Signal alternative).
A disturbance in the Force … #
This step is a little more complicated. We are greeted with two messages :
D@RK_StEL told me to send you the combination. I will send it to you via the usual method. All you need to do is knock on the server with the right combination.
Yes, I am ready to receive! Switching to stealth mode.And then a quite mundane and boring conversation (thanks huggingchat for generating a few empty dialogues) will start and loop over and over. Here is one excerpt :
conversation3 = [
"Have you watched any good movies or TV shows lately?",
"Yeah, actually! I just finished watching a really interesting documentary series on Netflix",
"Oh, which one was it? I'm always looking for something new to watch",
"It's called 'Explained'. They cover a wide range of topics from politics to science to culture",
"That sounds fascinating. Thanks for the recommendation!",
"No problem! By the way, how's your family doing?",
"They're all good, thanks for asking. My kids keep me busy with their sports activities though!",
"Ah, I remember those days. My daughter used to play soccer, and my son played basketball",
"Sounds familiar. Anyway, I heard there's a new restaurant in town. Have you tried it yet?",
"Not yet, but I've heard great things about it. The menu looks amazing",
"Same here. I think I might check it out this weekend with some friends",
"That sounds like fun! Let me know how it goes",
"Will do. Hey, have you ever traveled to Asia before?",
"Yes, I went to Japan a few years ago. It was an incredible experience",
"Really? I’ve never been, but it’s high on my bucket list. Did you visit Tokyo?",
"Of course! We saw all the famous landmarks like the Tokyo Tower, Shibuya Crossing, and Meiji Shrine",
"Wow, that must have been awesome. I hope I can plan a trip there someday",
"You absolutely should! Just save up some money and book a flight when you can",
"Good advice. Speaking of travel, where would you like to go next if you could choose anywhere?",
"Hmm...that’s tough. There are still so many places I want to explore. But if I had to pick one place, I’d say New Zealand. I’ve heard the landscapes are breathtakingly beautiful"
]First, you need to retrieve the conversation in a .pcap file.
from scapy.all import *
import socket
import tqdm
adresseIP = "20.19.38.158"
port = 2647
client = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
client.connect((adresseIP, port))
print("Connected to the server")
message = "THCON{I_H4V3_4_84D_F33L1NG_4B0UT_TH15}"
client.send(message.encode("utf-8"))
received = client.recv(1024).decode()
print(received)
for i in range(10,110,10):
received = client.recv(1024).decode()
print(received)
received = client.recv(1024).decode()
print(received)
_, filesize = received.split('-Size:')
filename = os.path.basename("recup.pcap")
filesize = int(filesize)
progress = tqdm.tqdm(range(filesize), f"Receiving {filename}", unit="B", unit_scale=True, unit_divisor=1024)
with open(filename, "wb") as f:
while True:
bytes_read = client.recv(1024)
if not bytes_read:
break
f.write(bytes_read)
progress.update(len(bytes_read))
print("Connexion closed")
client.close()
Next, we note that the ToS field in the IP protocol contains weird values. It is supposed to be constant and worth a value that indicates the type of service (phone, streaming…). These varying values are probably binary data that can be retrieved.
from scapy.all import *
scapy_cap = rdpcap('path/recup.pcap')
binary_string = ""
i = 0
for packet in scapy_cap:
if i % 2 == 0:
a = format(packet.getlayer("IP").tos, '08b')
binary_string += a
i += 1
bits = [int(bit) for bit in binary_string]
print(bits)
text = ''.join([chr(int("".join(map(str, bits[i:i+8])), 2)) for i in range(0, len(bits), 8)])
print(text)The result is : Port_The_Last_Jedi: 1337, Port_Rogue_One: 52377, Revenge_Of_The_Sith: 6666, Port_A_New_Hope: 1977, Solo: 1138, Phantom_Menace: 9991
Normally even if you haven’t seen the Star Wars movies (which you objectively should, at least except the Disney ones) you’d recognize the saga’s iconic names.
If we put the ports back in the order in which the Star Wars films were released, we get : 1977 - 9991 - 6666 - 52377 - 1337 - 1138
vim vs emacs). If you want my two cents, it made sense to watch them in the release date at some point to experience the plot twist. But since nowadays, everybody knows the twist of the Empire Strikes Back, I’d say the chronological order is superior. Anyway, back to the challenge …
The conversation tells us that we have to do a port knocking.
nc -w 1 20.19.38.158 1977; nc -w 1 20.19.38.158 9991; nc -w 1 20.19.38.158 6666; nc -w 1 20.19.38.158 52377; nc -w 1 20.19.38.158 1337; nc -w 1 20.19.38.158 1138;We get the flag : THCON{WHY_D0_TH3Y_N3V3R_KN0CK}
(Don’t forget to use a VPN for those on a filtered connection like the Renater one that was hosting the CTF.)
