What’s that about ? #
The THCon (Toulouse Hacking convention), is a French cybersecurity conference that brings together hobbyists, professionals and researchers every year at Toulouse in April.
This edition (2024), I was one of the challenge creators and (co-)created a few network challenges, a few steganography challenges, and mostly a full-blown 8 step OSINT challenge which was the backbone for the CTF lore.
Here is a summary of the challenge’s layout (in French sorry) :
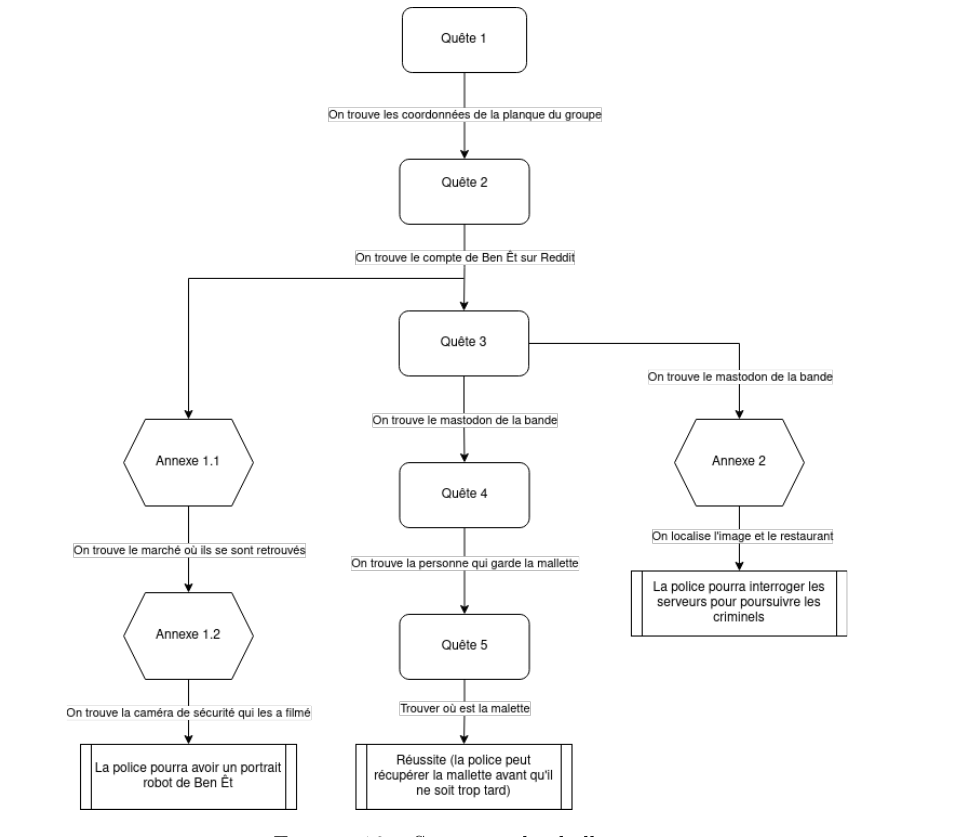
Note : the CTFd is not up anymore so if you did not participate, or you don’t remember the challenges you can take a look at https://ctftime.org/event/2269/tasks/
Step by step write-up #
Where the F...rench are they ?
#
The only information we have is a pair of telephonic station IDs to which the bad guys’ phone did connect. We can use the open-data platform of the French agency for frequencies and telecommunication : https://data.anfr.fr/visualisation/map/?id=observatoire_2g_3g_4g. This will give us two antennas, so we can search in between them (we would need a third one to perfectly triangulate, but it’s still already restricting the search enough) :
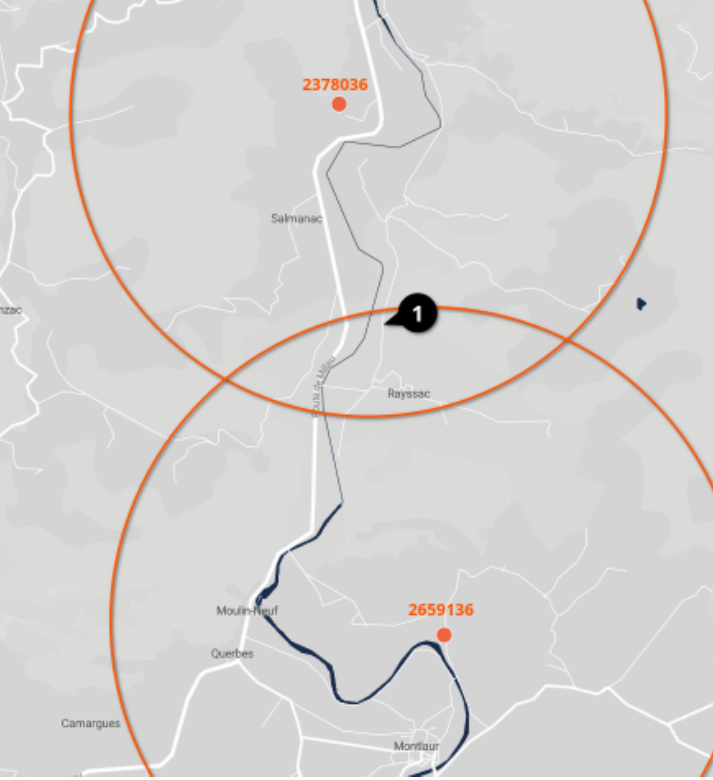
This leaves us with about 5-10 abandoned houses (and since the picture was taken IRL a reverse image search won’t work ^^’). It still does not take too much time to find that it is this building : https://www.openstreetmap.org/way/70292988
Flag : THCON{43.914-2.829}
That place's in the middle of nowhere
#
If you’ve found it through OSM, Turbo or another tool then the second step is faster, else you’ll have to search a bit to see that “Ben Êt” (whose name would be something like “Stu Pid” in English) created a node on it : https://www.openstreetmap.org/node/11662494898/history/3#map=19/43.914595/2.829335 and in the notes we see that someone else (Jacques) did tell him to stop breaking their cover by posting on his social networkS. We therefore search for the other social networks of Ben, but he actually has another name on the other social networks which is given on his profile page :
Aka ben_et_ on other social media.
We can then use one of the username search tools of https://osintframework.com/ or just try every social media and end up on https://www.reddit.com/user/Ben_Et_/
Flag : THCON{reddit-Ben_Et_}
Shall we play a (social) game ?
#
The next part is very usual, you just browse the profile of Ben and find a picture of a messy desk with a computer opened on an element chat with a QR code (those silly hackers …).

Scanning the QR code leads you to https://mastodon.darkbackdoor.thcon.party which is the internal social network for the hackers.
Flag : THCON{https://mastodon.darkbackdoor.thcon.party}
Like a sheep among wolves
#
You need to parse through the ≈ 600 messages posted on the mastodon to understand the plan of the hackers, if you read from the start you notice quickly that the hackers are doing meetings and publishing some minutes of these which are a gold mine of information. You can find those searching for the #minutes tag.
You discover that they are building a briefcase to carry the cryptographic keys used to encrypt the sattelites they hacked.
There was a lot of care given to continuity in this CTF, almost every challenge (keepass, cosmic rays, audio steganography …) was mentioned in this one in one way or another and tied to the global storyline.
If you liked the continuity and think it was great, or on the contrary think it did not bring anything, please give us some feedback on the Discord !
(There’s even a love story in it)
Once this is found you need to get the name of the person carrying the briefcase, you know from the minutes that there are some requirements to be the one carrying the briefcase :
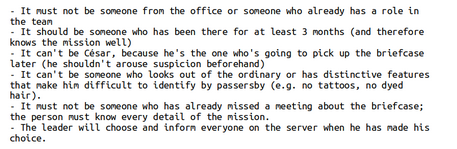
Flag : THCON{briefcase-eddydoncavapaslatete}
(fun fact his name would translate to “hey areyoucrazy”)
To infinity and ... down on earth
#
Now that you know what the plan is, you also know that the briefcase is to stay hidden somewhere for about a week. So the police needs you to find where it is, so they can retrieve it before the hackers do.
The minutes tell us it is a bin (a double-bottomed one to be more precise, the flag list should have also included this, sorry for those it bothered 😢)
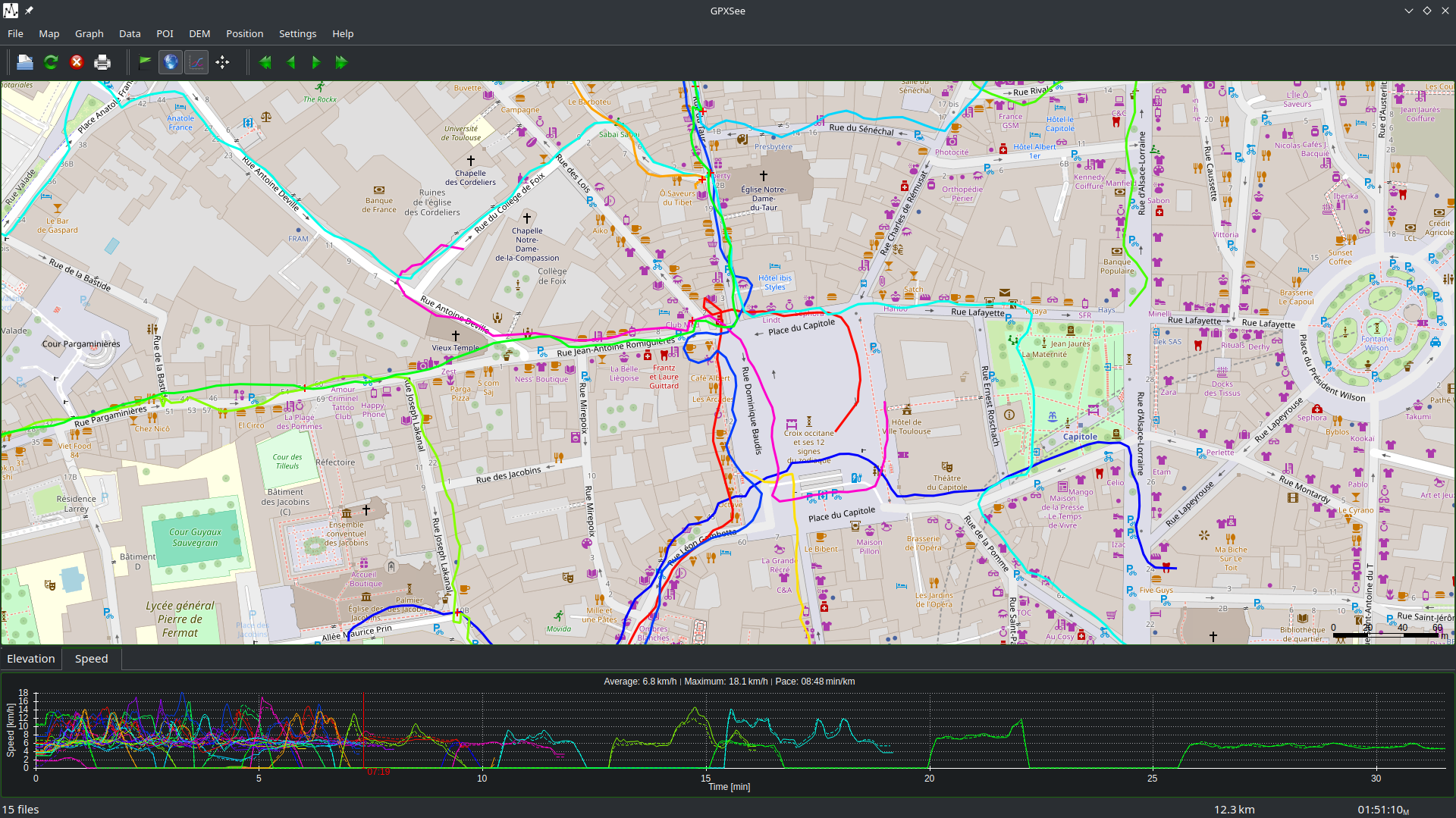
The second part of it is which bin. To find out you need to take a look at the GPS/workout tracking platform that the hackers use (and dumbly forgot to turn off when they carried the briefcase).
The leader of the group did give them instructions, so they could exchange the briefcase in the crowd of downtown Toulouse, and those who made the briefcase explained that transferring it from one person to the next takes about 3 minutes (since there is a mechanism that would wipe out the briefcase if somebody takes it from the current carrier). This way you could spot the transfer point out of the ~ GPS 15 traces (which fun fact took about 2 days of running and calculating to make with opentracks 🥵).
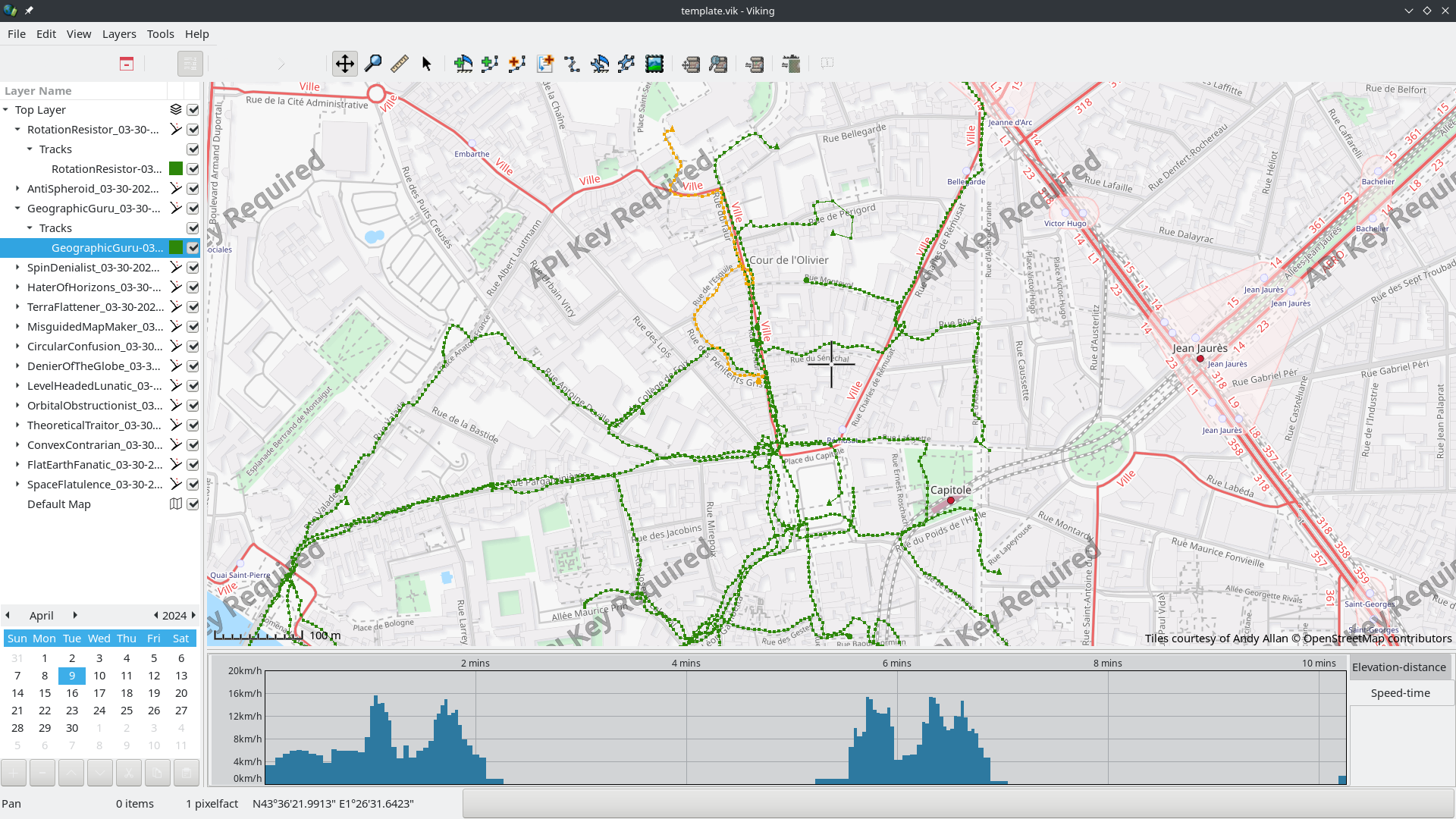
You could use tools such as GPXSee, Viking and a bunch of others :
For instance in the latter one (using viking), we can see that this person (whose trail is in orange) ran and paused twice for almost exactly 3 minutes each time, since you know who had the briefcase at first you can find out who had it last and where they put it. (And funnily enough the bin was created on OSM by Ben’s account too)
Flag : THCON{bin-11662494902}
👏 Congratulations to the 6 people/teams who did the whole challenge !
First Side quest #
Got a rocket for ya
#
We find on the reddit account of Ben that he met with someone at a market :
Dark Backdoor under surveillance
#
Once this is done all you need to do is locate precisely which part of the market can be seen on the picture and from which angle, then head out to surveillance under surveillance to find the id :
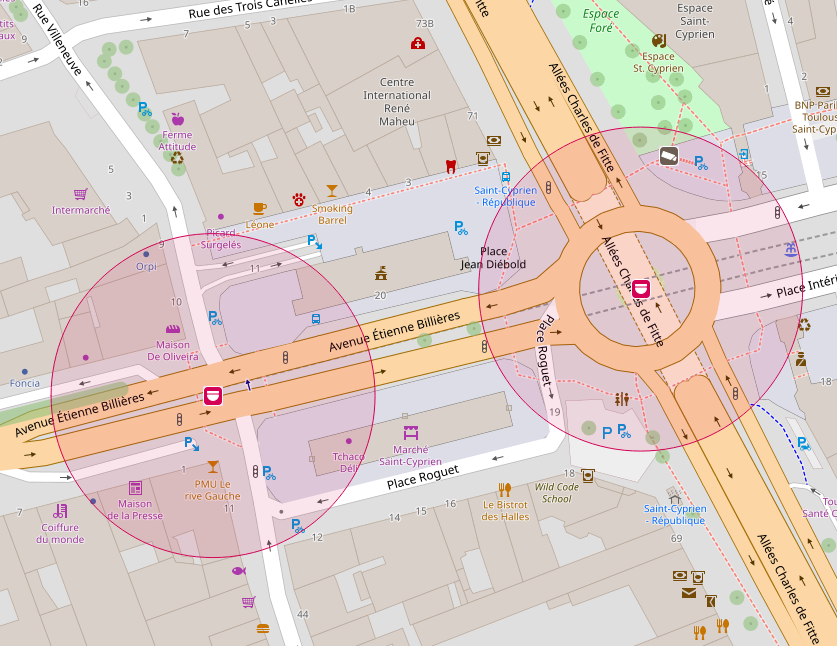
Second Side Quest Le dîner de cons
#
If you look at the mastodon you end up finding this message. It tells us that they ate some crêpes near the hotel where the picture was taken.

This one was a trap ! 🙀 If you reverse-search it, it takes you to the United States because it is a well known picture. If you download the picture (which weirdly is not published on mastodon but shared with a link, … weirdly enough !) and inspect it, it still has some location metadata !
Actually, the Ibis hotel has it on the front of their building, and that’s where the picture was taken ! Once this was found it is just a matter of finding the crêperie one of the most well-renowned crêperie in Toulouse.
The name of the challenge comes from a famous French comedy : https://www.allocine.fr/film/fichefilm_gen_cfilm=16731.html
Technical points #
This project was not only interesting in terms of OSINT, since I have had to create a (cheap and bad-looking) ripoff of Strava for the last step which automatically created a timeline of runs from various GPX traces. I also had to implement GPX modification software (especially one script to offset a whole GPS trace to a particular date). But the most interesting part was to deep dive into how mastodon (an alternative to X) works in order to fake the 600+ messages that were posted by the villains.
I developed an automated tool that posted the messages in the right order and associated the messages posted (through their IDs) with their dates (with specified or randomized delays between the replies). This could then be used to fake the date by replacing the date values directly in the database of our mastodon instance. See the blog post about the tool :