Hello,
This is the write-up of most of the challs flagged by my team at the Oxyhack Cyberevent CTF. Though I at least took part in those challenges, some write-ups are from other teams members.
We finished first in this quite easy but still cool regional CTF (apparently the PEDA team was the team of the school’s teachers. Quite happy to manage to get first place then !) :
Steganography #
The Quest. #
Well… it’s a non-standard weird windows software I had never heard of 🤷 (https://www.openstego.com/) maybe the reason this was the last steganography challs to be flagged
OHxY{UnC0v3r_th3_c0nc34l3d_tr345ur3_w1th1n_th3_d1g1t4l_l4byr1nth}
Hey BOB ! #
The description hints at LSB steganography.
One simple way to test this is to use Aperisolve which combines a lot of tools. I personally just ran zsteg on my exegol container and found the following :
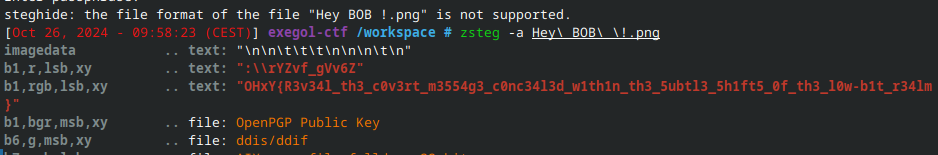
OHxY{R3v34l_th3_c0v3rt_m3554g3_c0nc34l3d_w1th1n_th3_5ubtl3_5h1ft5_0f_th3_l0w-b1t_r34lm}
Alien Sound ? #
Audio file $\Rightarrow$ First reflex should be looking at the spectrum to find anomalies. Even if there can be WAW Header injections or LSB steganography, most easy challenges can be solved that way.
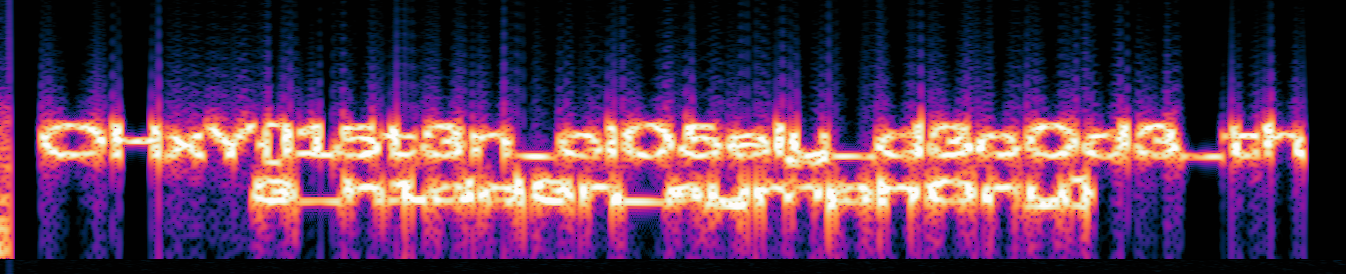
OHxY{l15t3n_cl05ely_d3c0d3_th3_h1dd3n_symph0ny}
Web #
Shout out to Thomas Hernandez (a.k.a. Daresse) with whom I had to understand the weird intent of Cookie Mayhem
Trickery! #
We first have a blank webpage with just an input. First try to put innocent data in there. We get redirected to a page where the data we gave is printed.
First things to try in this scenario are : XSS (<script>alert();</script>) | SSTI({{1+1}}) | command injection(; whoami).
Here SSTI gave us the flag instantly :
OHxY{3xpl01t_5ST1_f0r_tr1umph}
Cookie Mayhem! 🍪 #
This one lives up to its name. Guided by the name of the challenge we go straight into the cookies, and we only find one, the session cookie :
eyJlbmNvZGVkX2ZsYWciOiJleUpoYkdjaU9pSklVekkxTmlJc0luUjVjQ0k2SWtwWFZDSjkuZXlKbWJHRm5Jam9pUkRGa1gza3dkVjlyYmpCM1gyMTVYelV6WTNJemRGOF9JbjAuWllvREFZN2FranZUcEt3YWg3ekZES01fYmQ5V2pKdFY1QTY2VDEyTm11OCJ9.Zxyp6A.HsKdzaEsgskm8vl1p8B3AXQnP-IWe recognize a signed JWT token (B64string.B64string.B64string = Header.Payload.Signature) so let’s put it in jwt.io to analyze it. The payload and the Signature
don’t give us anything interesting but inside the header we find another JWT token. What is a JWT token doing in the header of another JWT token ? Nobody knows but here it is:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJmbGFnIjoiRDFkX3kwdV9rbjB3X215XzUzY3IzdF8_In0.ZYoDAY7akjvTpKwah7zFDKM_bd9WjJtV5A66T12Nmu8This one is completely normal though, and its payload contain a flag :
D1d_y0u_kn0w_my_53cr3t_?
This flag isn’t the flag we are looking for but a hint, meaning we have to find something else.
The challenge description mention that we are allowed to enumerate the website, so we run feroxbuster, looking for directories. After a few minutes it comes up with a /check page which have a form with two fields we can write in:
JWT token:
Secret Key:Still using jwt.io we re-craft the “normal” JWT token using the same data and algorithm but our own Secret Key. We send this new token and our own secret key inside the form, and we get the flag :
OHxY{M4n1pul4t3_JWT_5e5510n5_w1th_5STI_pr0w355}
