Hello there,
Last blog post about the Oxyhack Cyberevent CTF with this time the write-ups for the forensics/network challenges.
Forensic #
Lost in Transmission #
You just have to open the file with wireshark and when you take a look in the HTTP exchange, you can see the flag.
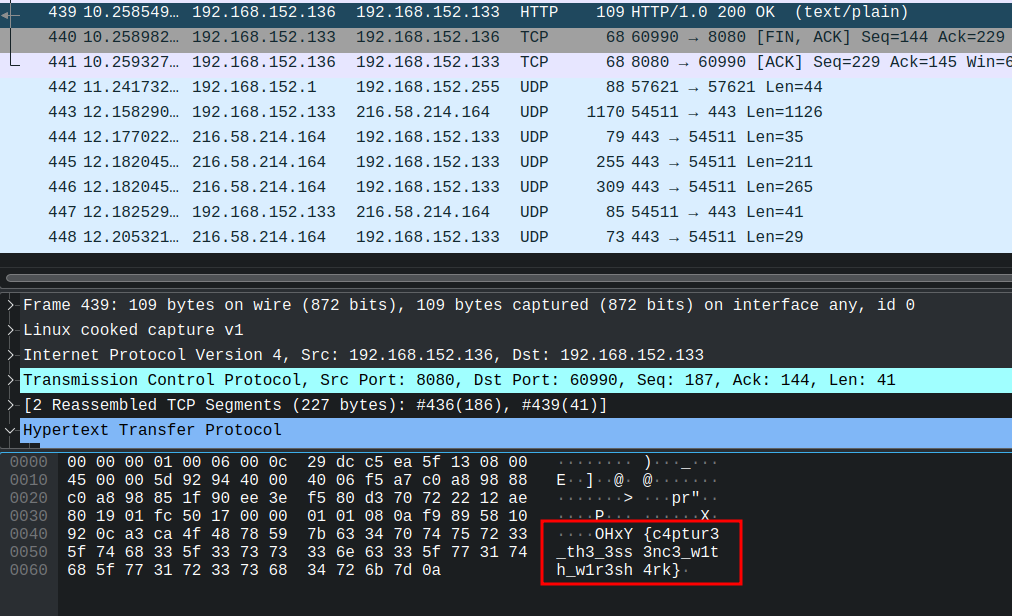
OHxY{C4ptu3_th3_3ss3nc3_with_w1r3sh4rk}
Zip #
Shout out to Baptiste Rebillard for this one.
In order to read home.img, we’re going to mount the partition
sudo mount -o loop home.img /mnt We notice a file named “flag.txt” in /mnt/jim/Documents
In /mnt/jim/ :
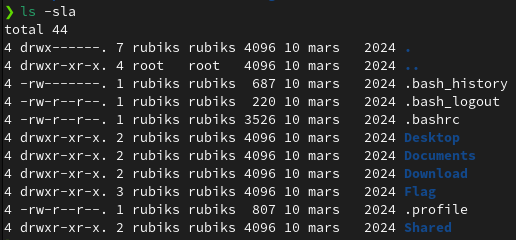
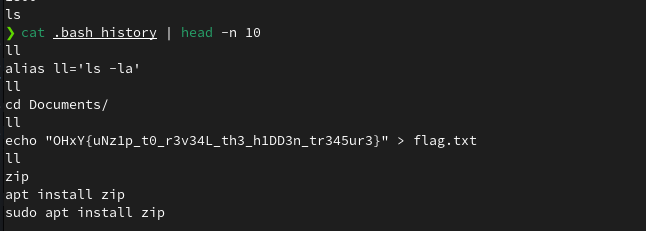
So we don’t have to unzip :+1:
OHxY{uNz1p_t0_r3v34L_th3_h1DD3n_tr345ur3}
Reassemble-the-Unknown #
We have a .pcap file with some noise mixed with relevant information, let us first remove all UDP/TCP garbage.
from scapy.all import *
import socket
scapy_cap = rdpcap('file.pcap')
a=b''
# run over all packets
for packet in scapy_cap:
# filter
if packet.haslayer(ICMP) and (packet[IP].len != 60):
print(packet[Raw].load)
a+=packet[Raw].load
with open("image.jpeg", "wb") as fichier:
fichier.write(a)We are left with some data that looks like a picture and then some random strings. In the code aove we exclude the strings that do not seem ot be very insteresting.
The image is actually a JPEG with EXIF (as can be seen based on the magic bytes). And it looks like the chall devs are trolling us :

A quick inspection shows us there is a comment that may be useful :
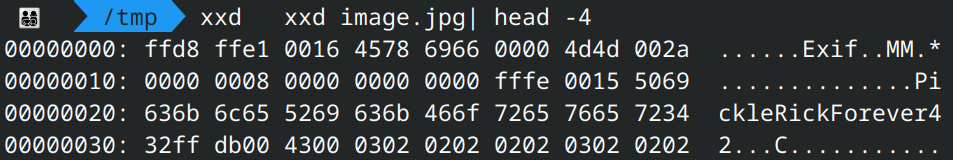
You can also see it on an aperisolve run or just by running exiftool directly.
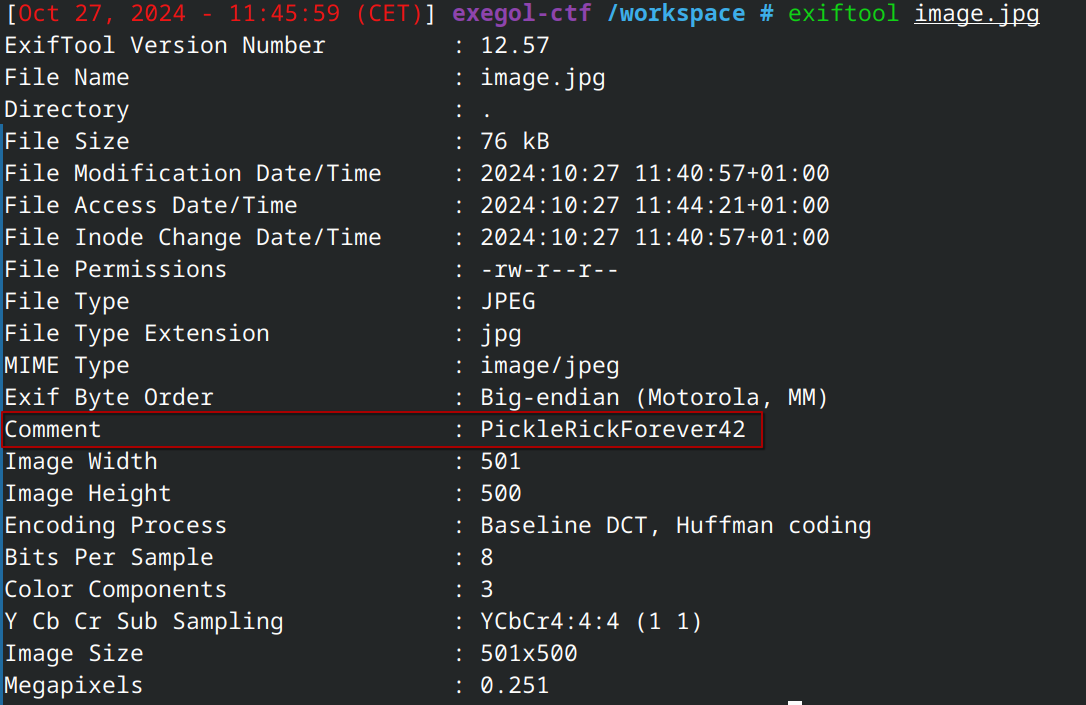
Using this (PickleRickForever42) as a password, one can run again the programs that take passwords as inputs to see if there’s anything of interest.
Steghide gives some interesting result since it grabs a flag.txt file.
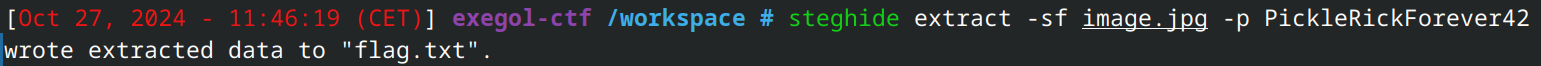
OHxY{R3c0nstruCt_Th3_Fr4gm3nt3d_Ech0}
