What’s that about ? #
The THCon (Toulouse Hacking convention), is a French cybersecurity conference that brings together hobbyists, professionals and researchers every year at Toulouse in April.
This edition (2025), I was one of the challenge creators and created a 6-part geosINT challenge, a few steganography challenges, as well as making all challenges lore-accurate.
Note : in the case the CTFd is not up anymore, if you did not participate, or you don’t remember the challenges you can take a look at https://ctftime.org/event/2660/tasks/ although not all of them may be listed sadly :/
Global explanation #
In this challenge we learn that the XSS (the baddies) have managed to take control of the THCon’s socials ! We need to piece back images that they have posted on the THCon’s socials :
Precise Step by Step #
So, this is socINT, we have two things to check first :
- All the official THCon accounts (listed on the website)
- Any social not listed on the website using a tool such as https://namechk.com/
If we start with the obvious socials (this challenge is marked as steganography let’s remember !) we can list the official accounts :
- X (formerly Twitter)
- Mastodon (but that one is a mirror of Twitter)
- YouTube
If we look at The most obvious ones we get :
- Nothing on YouTube
- A thread on X (formerly Twitter) 🥳🥳🥳
- A post on LinkedIn that links back to a picture on the website
Let’s take a closer look :
The thread is quite simple and contains two images :
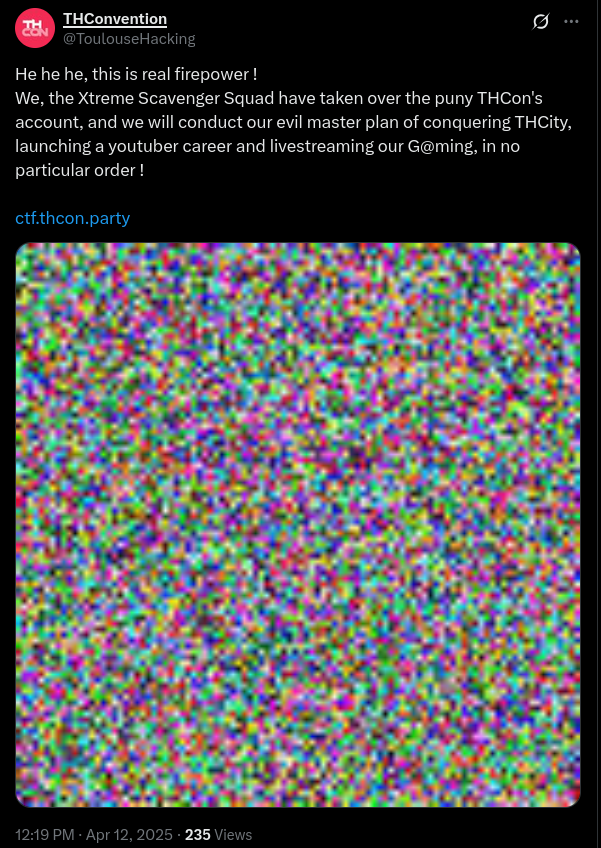
In it, we learn that the XSS are playing games such as LOL or Marvel Rivals (great, probably not useful) but we also get two files. At this point the steganography part starts, and we can take a look at the files.
A few remarks :
- These are noise files
- The bigger file has dimensions
1000x1000while the smaller is100x100 - the bigger file seems to contain 10x10 repetitions of some noise pattern
- They seem to be created by a tool or something (hence their weird format when being analyzed)
One first though would be to xor the images together and since the bigger file seems to be a repetition of smaller noise, we can try xor-ing the bigger file with a repeated smaller file.
Here is a POC python script that does exactly that :
from PIL import Image
noise100x100 = Image.open("./noise.png")
pixel_noise100x100 = noise100x100.load()
im = Image.open("./hidden-image2.png")
pixel_image = im.load()
for i in range(im.size[0]): # for every pixel:
for j in range(im.size[1]):
r,g,b,_ = pixel_image[i,j]
# r,g,b,_ = pixel_image[i,j] # Sometimes platforms (such as Signal) add a transparency
r_x, g_x, b_x = pixel_noise100x100[i%100,j%100]
# r_x, g_x, b_x, _ = pixel_noise100x100[i%100,j%100] # Sometimes platforms (such as Signal) add a transparency
r = r ^ r_x
g = g ^ g_x
b = b ^ b_x
pixel_image[i,j] = (r,g,b)
im.save("./out.png")When we xor the image in the X thread with the smaller noise sample from the same thread we get :
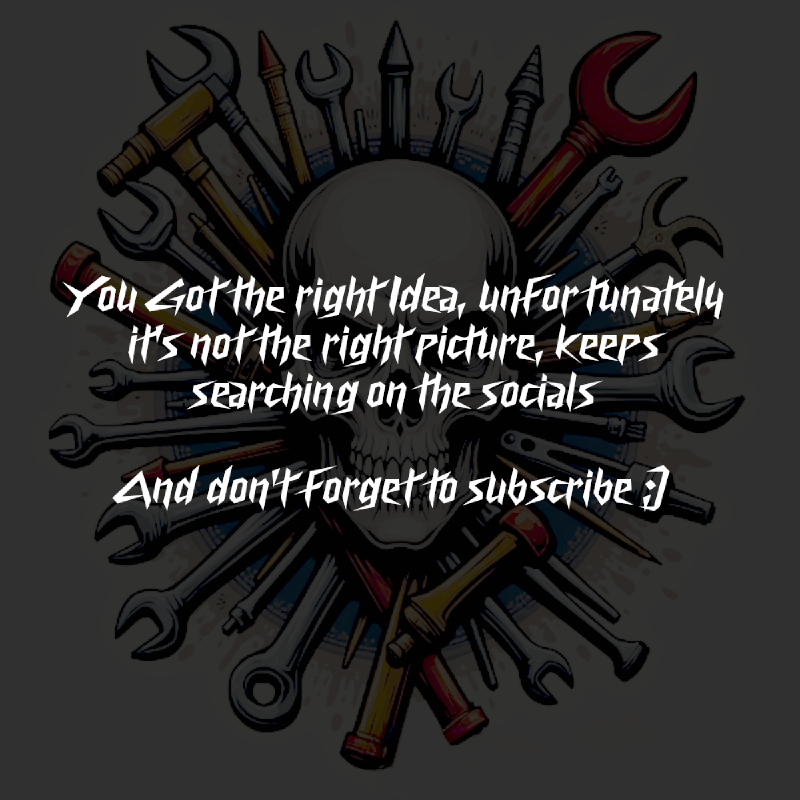
We then use the picture we found in the LinkedIn post to get :

Resolutions #
I saw people do a lot of crazy stuff with this like xor-ing the picture with itself but with the offset (so that the columns of noise cancel one another) or xor the two biggest noise images which gave them a superposition of both image, that was really fun 😅
Congratulations to the 6 that flagged it !