What’s that about ? #
This week I had quite some fun with the Try Hack Me Hackfinity CTF (although I could not spend that much tim on it sadly). Here are the flags I got :
Notepad Online #
When logging in as noel we are greeted with a fairly simple notebook, which uses a direct id reference.
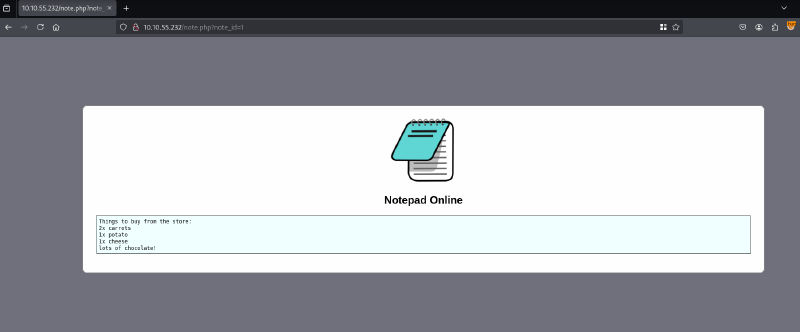
Since this is an easy challenge and the id really is suspicious, before fuzzing or trying to fiddle with the different types of requests we can use, let us check for IDORs :
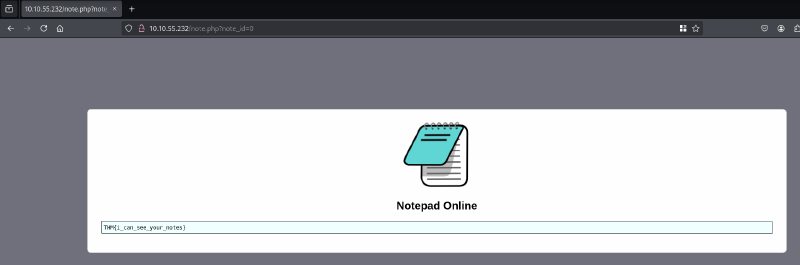
Well that was unexpectedly fast !
THM{i_can_see_your_notes}
Dark encryptor #
We play around the inline PGP encryptor and find a weird behavior with quotes : This is characteristic of either an SQLi or a command injection :
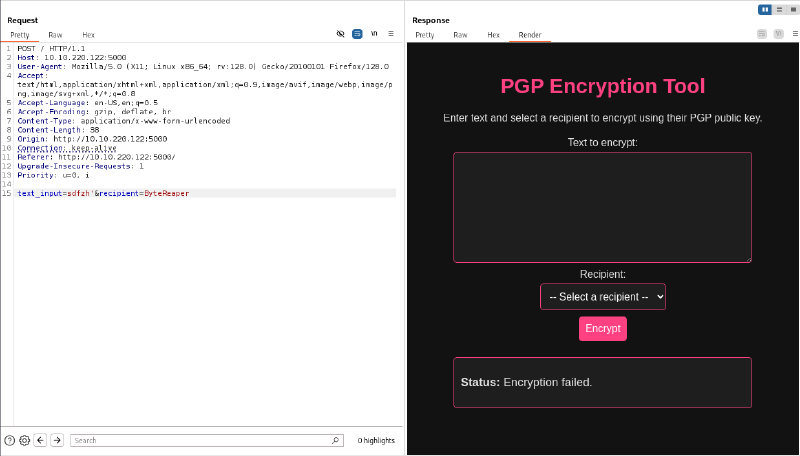
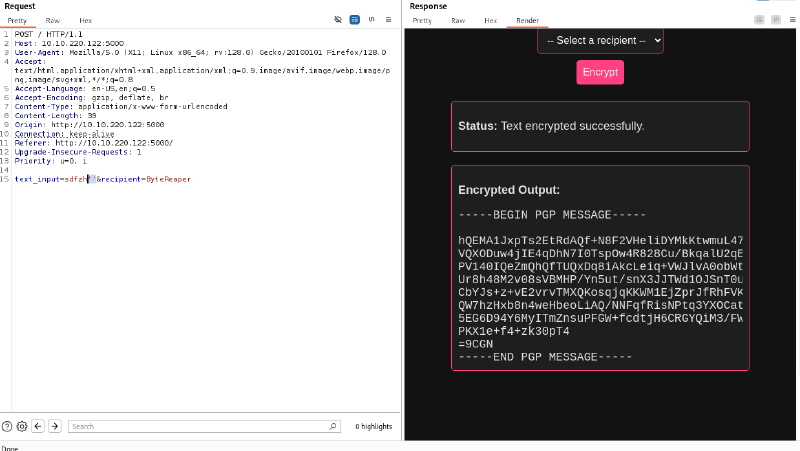
It looks like the back-end is running some kind of command like this without properly sanitizing it :
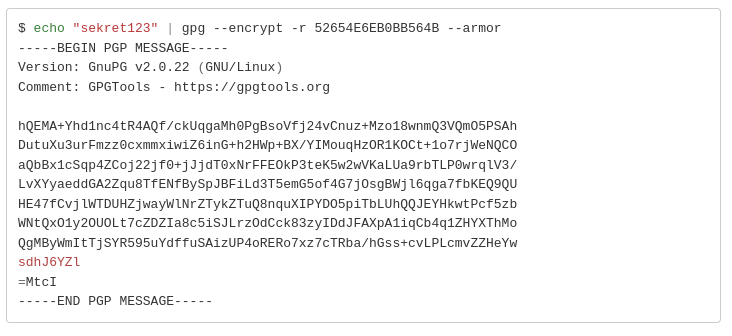
If we attempt to get some feedback with an ls or a sleep nothing happens, so either these are filtered by the application or our string is not executed.
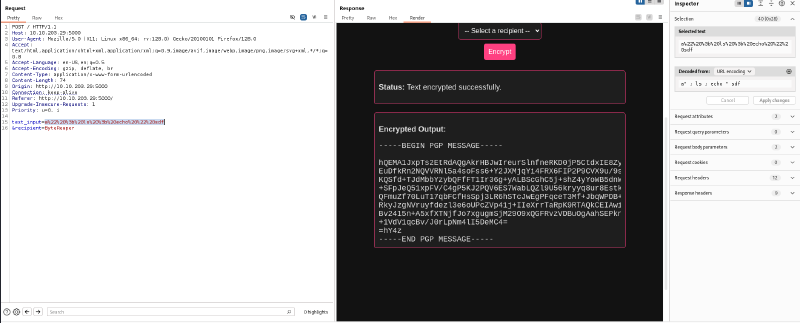
If we input only a semicolon (;) as the message we get the “Usage” error message which confirms that the app is using a bash back-end and inputting our request inside an unsanitized python call with the syntax detailed in the answer.
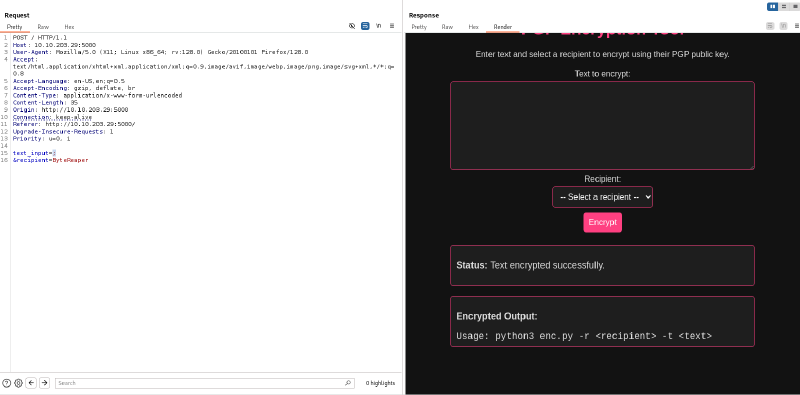
Therefore, if we add an echo command, the output of this will also be added to the display of the web app :
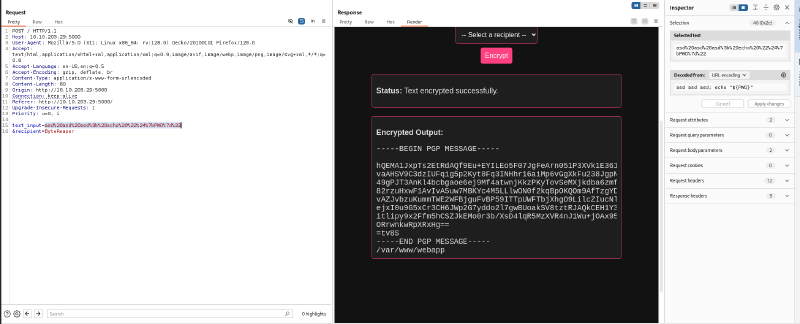
We can use this to cat the flag out :
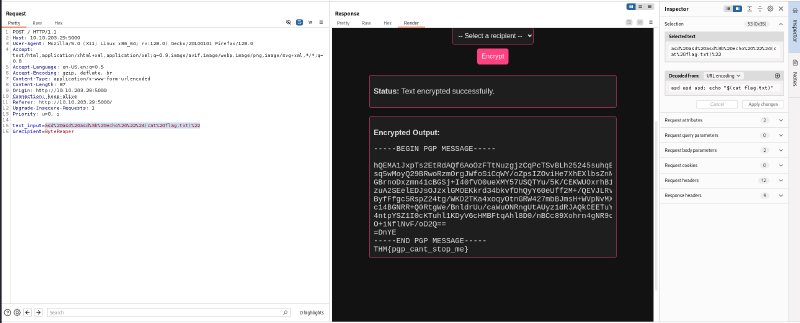
THM{pgp_cant_stop_me}