
What is CPTS ? #
CPTS is a certification by Hack The Box. It is quite similar to the OSCP in terms of difficulty, although the exam is quite different (10 days everything included instead of 24 hours for the OSCP exam, you need to complete the course first, no tool restrictions …). HTB describes it as :
The HTB Certified Penetration Testing Specialist (aka HTB CPTS) is a highly hands-on certification that assesses the candidates’ penetration testing skills. HTB Certified Penetration Testing Specialist certification holders will possess technical competency in the ethical hacking and penetration testing domains at an intermediate level.
My overall feedback on the course + exams #
Great course material #
As previously stated, the completion of the course path is required before you can start the exam. This course, when followed seriously (taking notes, reading the whole thing etc.) should in my experience take about 3-6 months, depending on your level at the start. There are also optional modules to get the basics (basics of networking, Linux, Web, AD etc.)
Here are a few stats they give you when you’re done with the course :
- Around 250 Targets hacked
- 400+ module sections completed
- 500+ challenge questions solved
- Over 750,000 words read
As someone with a bit of experience in offsec (through academic courses, and personal training on platforms such as rootme) I found that the courses still contained a lot of interesting information I did not know or did not understand fully. The courses were really high quality and if you take the silver subscription as I did, you have corrections which is a huge time saver and doubles down as an explanation of things you may have missed when reading the course.
A technically challenging exam #
I would say that this exam is quite perfect in the sense that it tests pretty much every.single.thing. you learned while still evaluating you on your understanding, methodology, and reflection. This is definitely not the type of exam that you will pass just by copy-pasting what you did in the exercises as the exam.
As of now there seems to be a bit more than one thousand people that have passed this certification, so it is probably less valuable if what you want is for HR and recruiters to notice you. But in terms of technical recognition it seems to be one of the best for the intermediary category. There is an interesting article from 0xP about this.
Advice #
When preparing #
Crash test #
I’d recommend you do AEN blindly. What does that mean ?
AEN (Attacking enterprise Network) is the last module of the path. It is a step by step, guided attack on an enterprise network and looks close enough that it can give you a good idea of whether you’re ready for the Exam. Doing it blindly means you only read the first page, start the machine and approach it without following the step-by-step tutorial. You only need to know that you need to get Domain admin on the AD + root on another machine accessible from there.
Then, when you’re done (or stuck, in which case I recommend you go as far as needed to overcome your blocking point then move forward) do it with the step-by-step and take note on a sysreptor instance.
In the real exam you’ll have 14 flags (12 of which you need to find to pass the technical part of the exam), scattered over a bit more machines but if you want to prepare for the scale you can take a look at the Zephyr Pro Lab (which is noticeably bigger than the exam).
Prepare your notes #
I’d recommend taking notes of all courses you take on academy + every exercise/CTF/machine/… that may be relevant. I did mine with Logseq and obsidian and I recommend using one of those two, or something that has equivalent functionality (and is NOT stored online for obvious confidentiality reasons).
Two habits that I took and that really helped me were to take high level notes of a technology/service (ex : WordPress, Splunk, Joomla, osTicket, SSH, FTP), and having on another page (linked using Markdown links) a methodology bullet point on “How to attack XYZ”, which you should be able to follow blindly. The point of this being not to follow it blindly, but to grab the low-hanging fruits efficiently.

Something else I’d recommend would be to link your topics together as you can see in the picture above. Like linking the page explaining the dumping of NTDS to the page of your tool (NetExec for instance) and the page of password cracking. This can save you a lot of time, as you don’t have to go hunting for “that other page I forgot how I named”.
Prepare reporting #
Another thing I’d recommend is to use sysreptor. sysreptor is a reporting tool for which Hack The Box has built an official template.
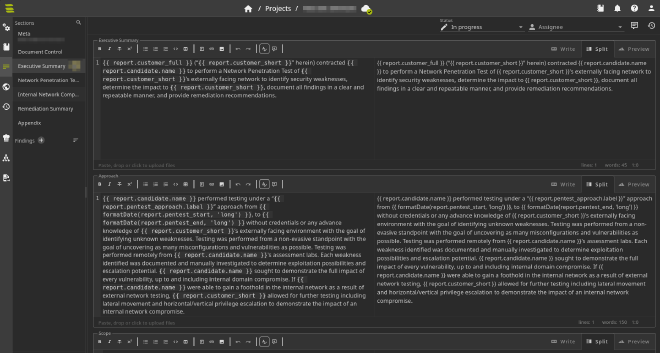
You can already create templates for all vulnerability that you think are likely to uncover. And if you have the time to do so, I’d recommend writing as many finding templates for vulnerabilities you learned about in the CPTS course. Trust me it’s will you a lot of time, so you don’t have to write 20+ vulnerabilities at 3AM on the last night before your submission deadline. (If this sound personal, that’s because it is)
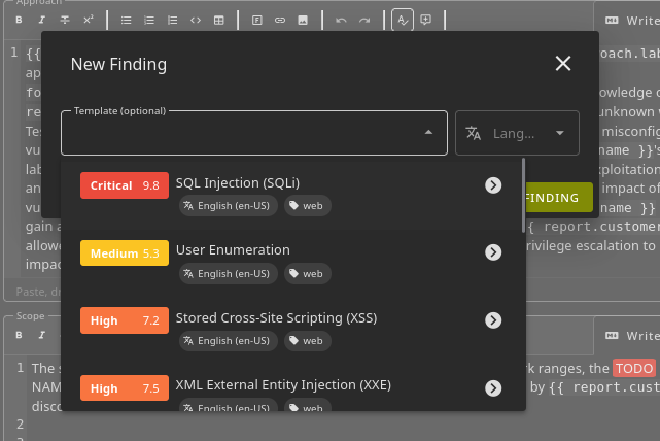
I really recommend installing sysreptor locally (because this way you have unlimited features) and learning how to use it. You can follow their tutorial there. With the local versions you can already write pre-made vulnerability notes.
I’d recommend taking a look at this reporting methodology and build your own methodology based on this beforehand (every moment you spend before the exam is time you’ll be able to use during it)
When taking the exam #
Keep track of what you do #
As you can see on AEN the attack surface is quite large, which means that if you rely solely on what you remember doing you’ll end up doing the same thing over and over again.
My advice on this is : Take note of everything. Especially take notes when you tried something that did not work. It would be a shame that you do it again in 5 hours or the next day because you forgot that you already tried it.
Another good habit to take : Fill your loot folder with even the smallest things, you’ll thank yourself 10 hours later because you won’t have to spend 15 minutes doing an exploit all over again just to get some info / file / secret that you overlooked.
Report methodology #
If you’re ready from a technical standpoint, this is the most important thing to spend time on. HTB grades you on the report, and a bad reports means a fail no matter your technical achievements. After all it’s the product the client looks for.
I ended up having a methodology a bit differently from the one mentioned above and relied way less on AI, except for writing my vulnerability pages. I did look at the benchmarks at the time which placed Google’s Gemini first and Twitter’s Grok second (amongst free options) and after getting them both to write a full vulnerability template I settled on Grok which had the best-sounding wording and style - at least for the limited usage I had.
Pentest methodology #
I highly recommend you keep a markdown “todo” list with checkmarks ( - [ ], both logseq and obisdian support it) whenever you get an idea of something you could do. This way, when you discover something new (a new vhost, machine, user account, the result of a scan) and have 5 ideas of things you could test, you’ll end up testing all 5 and not the first 1 or 2.
I would also recommend doing a network graph with all the open ports and the position of the machines (and of your pivots). For the pivoting part I used ligolo-ng which I highly recommend also, but use whatever you are most comfortable with. Just make sure you know how to use tools that don’t play very well with it like bloodhound :
Getting yourself out when you’re stuck #
When in trouble remember everything you will ever need is mentioned in the course material. This is what makes it even more frustrating at times when you flag, and you are not even happy as you realize how dumb you were.
So use the Hack The Box search functionality, and also make sure you have good quality notes that you can rely on and search through. If it does not work look for modules that could be related to what you do and skim through them. You can also use sites such as https://ippsec.rocks and https://ctfsearch.com. Especially the first one gave me some ideas during the test which sometimes enabled me to move past a step I was stuck on.
If when you’re stuck on a flag you think about searching for flag X in the discord chat, let me spare you some time by summarizing everything you’ll find :
guy1 (doing the CPTS) : I'm so stuck on flag X it's so hard
guy2 (answering) : Go back to the lectures, it's in there. Once you see it you'll see it's easy. Think simpler and go over everything you have and can do.
[optionnal, 5 h after] : guy1 : Oh damn I'm so dumb, it was right in front of me that whole time. Haha. LOL.
Sometimes there will be rabbit holes, and it is hard to give proper advice on that, but stick to the “get the low-hanging fruits first” principle. Basically start with the tings that look simpler, for instance, check if you are a sudoer or can run a command with sudo -l before setting out to find a 0-day in the Linux Kernel.
To sum up : Be ready to dig deep but keep an eye out for simple things first.

Managin the stress #
I recommend taking some breaks on a regular basis. Whenever you don’t know what to do, you are going in circles, or you are running a long scan, take the opportunity to do have a short rest.
Trying to do something that does not involve a screen helps a lot, even if it is only for 5 to 10 minutes (like going our for a 5 minutes walk, going outside, reading a chapter of a book, calling/chatting with someone, saying a decade or perhaps even taking a short nap if that works for you).
Keep in mind that the exam is not a smooth sailing ride, and thus be prepared to get three flags in a few hours but then get stuck on another one for a day and a half. Every one is different so try not to focus on what the others tell you on flag X (my hardest flags were 9, 2, 1 and 12 in that order, you will probably experience something different)

Another thing that worked quite well was to use the infamous “plastic duck” technique (It does not have to be a plastic duck it can also be another figurine, your dog, your right monitor or if you are next other people just someone you imagine, although speaking out loud seemed to work better for me). I would describe in great precision what issue I had, what I had tried and this helped tremendously.
Writing the report as you go (either in your notes or in your final report) also helped since you have to describe, and it can make stuff clearer in your head.
What happens after ? #
When you submit your lovely little (mine was 105-ish) report, HTB will grade it and give you an answer within 30 working days (about 40 full days). The wait can be a bit long, in my case I got it on the 39th day or something of this type.

Note that if you fail you will re-take the same exam and thus start from where you left off (at least if your note-taking was good). The voucher you buy is worth two trials as long as you take the second exam shortly after (check on HTB website for the exact date & time things, it looks like they sometimes change).
You will now be able to register your certification on the Hack The Box discord so you get a badge next to your name (because cosmetics are cool). And if you want to, you can buy a CPTS pack containing a T-shirt, printed certificate, pins and sticker. Because as my former teacher and friend Benoît Morgan once told me : “(free) corpo cybersec swag is best swag” 😂